Privileged Access Management
Our Privileged Access Management (PAM) solution takes over every aspect of your IT infrastructure. It helps you to make contextual security around your most critical asset which is your business data.
Its granular access control lets you shape your security infrastructure the way you like.
Apart from that it gives and revokes access for whomever you wish, whenever you wish, all on your terms.
Privileged Access Management
Control Access to Your Data
Secure your Data from Anywhere
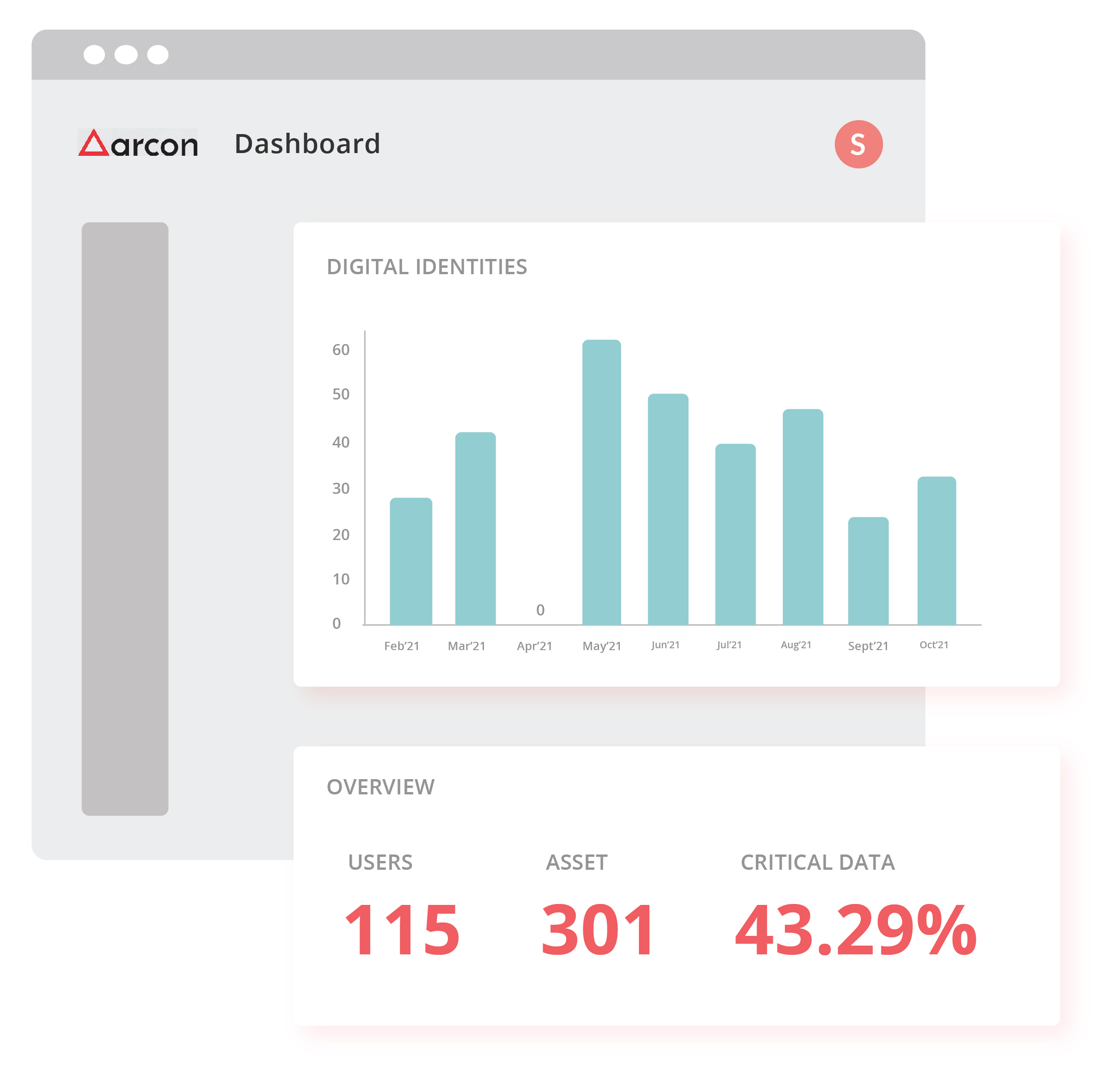
Privileged Access Management
Major top features of ARCON | PAM
01.
Password Vault
PAM offers a highly secured password vault. This vault generates strong and dynamic passwords and revolves them automatically.
02.
Ephemeral Access:
Apart from that it automatically makes rules and role-based temporary access rights with an Amazon Web Services (AWS) Console or Command Line Interface (CLI) component.
03.
Virtual Grouping:
PAM also provides a dynamic group setting with virtual grouping. In this grouping, you can create functional groups of various systems.
04.
Session Monitoring
PAM provides basic audit and monitoring of all confidential activities via a single command center in real-time.
05.
Session Monitoring
PAM provides basic audit and monitoring of all confidential activities via a single command center in real-time.
06.
Single Sign On:
It helps to connect to a distinct category of systems and devices without entering login credentials
07.
Security Compliance Management
The ARCON | SCM solution makes and implements a complete IT risk management framework. It is a suitable engine for all IT risk management controls needed to be implemented at various layers for effective risk mitigation. PAM makes sure the creation of a strong security posture and ensures adherence. Leave IT Risk Assessment to the bots crucial technology platforms need a continuous risk assessment. This can be accomplished through the power of AI – governing, assessing, and optimizing the organization’s Information Risk Management
08.
Endpoint Privilege Management
The ARCON | Endpoint Privilege Management solution (EPM) provides endpoint privileges ‘just-in-time’ or ‘on-demand’ and observes all end users for you. The tool sees insider dangers, compromised uniqueness, and other nasty attempts to breach endpoints. EPM comes with a powerful User Behaviour Analytics feature that takes note of the normal conduct of end users and recognizes atypical behavior profiles and other entities in the network.
09.
Privileged Access Management Lite
This solution is Ideal for startups and SMEs. Our cloud-based ARCON | PAM Lite solution stores your credentials with best-in-class encryption in an unbreakable Password Vault. The pay-as-you-go structure and zero set-ups time mean that it is weighty on elements but light on your pocket.
10.
Save Time on Deployment and Maintenance
It containerized setup based on microservices. Apart from that, it takes no time to be installed in your company's infrastructure with a seamless maintenance method that does not involve any hardware repair.
11.
Optimize Cost Spending
It lights on your pocket, needing you to invest nothing upfront on a big security set-up. A pay-as-you-go structure that allows you to save on endless software licensing overhead expenses and only pay for what you use
12.
Access it Whenever you Need to
Our solution is accessible for you whenever you need it, without the requirement for admin or technical support to be present to make it work. On top of that, it can be deployed from anywhere on the planet and needs zero downtime.
Privileged Access Management
Key features of ARCON | PAM Lite
01.
Fine-Grained Access Control
It reduces the risk surface by providing the deepest levels of granular control over confidential users through a rule- and role-based, centralized governing policy.
02.
Multi-factor Authentication:
PAM Lite offers OTP validation that combines disparate third-party authentication solutions to set identity references.
03.
Password Vault
Next thing it offers an admiringly safe password vault that causes strong and dynamic passwords and rotates them automatically.
03.
Session Monitoring
It also provides basic audit and monitoring of all privileged actions through a single command center in real-time.
03.
Audit Trails & Reporting
Last but not the least, it provides a full audit trail of privileged actions by recording every command/query executed by end-users in text and video format.