SSO Secure Server Email Login: Guide to Secure Your Emails
In today’s digital world, email has become an integral part of our personal and professional lives. With the increasing risk of cyber threats, securing our email communications is of utmost importance. Single Sign-On (SSO) combined with a secure server is an effective solution to enhance email security and protect sensitive information. In this blog post, we will explore the concept of SSO Secure Server Email Login and discuss its benefits and implementation.
Understanding SSO and Secure Server Email Login
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications or websites with a single set of login credentials. It eliminates the need for multiple usernames and passwords, making the login process more convenient and user-friendly. A secure server email login ensures that the email communication between the server and the user remains encrypted and protected from unauthorized access.
Importance of Secure Email Communications
Emails often contain sensitive information, including personal details, financial data, or confidential business communications. Without proper security measures, these emails are vulnerable to interception, data breaches, or unauthorized access. By implementing SSO combined with a secure server email login, you can significantly reduce the risk of data leaks, identity theft, and other cyber threats.
Benefits of SSO Secure Server Email Login
a. Enhanced Security: SSO adds an extra layer of security by implementing robust authentication mechanisms, such as multi-factor authentication (MFA) or biometrics. Combining SSO with a secure server email login ensures end-to-end encryption of emails, protecting them from prying eyes.
b. User Convenience: With SSO, users no longer need to remember multiple login credentials. They can log in to their email accounts using a single set of credentials, saving time and reducing the likelihood of forgotten passwords.
c. Centralized Access Control: SSO provides centralized control over user access. Administrators can easily grant or revoke access to email accounts, ensuring only authorized individuals can access sensitive information.
d. Simplified User Management: SSO simplifies user management for organizations. When an employee joins or leaves the company, their access to email can be easily managed through a centralized SSO system, reducing administrative overhead.
Implementing SSO Secure Server Email Login
a. Choose an SSO Provider: Select a reputable SSO provider that offers robust security features and integrates well with your existing email server. Some popular SSO providers include Okta, Azure AD, and OneLogin.
b. Configure SSO for Email Login: Follow the documentation provided by your chosen SSO provider to configure SSO for email login. This typically involves integrating the SSO provider with your email server and configuring the necessary authentication protocols.
c. Enable Secure Email Protocols: Ensure that your email server supports secure protocols such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS). These protocols encrypt the email traffic between the server and the user, preventing unauthorized interception.
d. Educate Users: Conduct training sessions or provide documentation to educate users about the new SSO secure server email login process. Emphasize the importance of strong passwords, avoiding phishing emails, and other best practices for email security.
Best Practices for SSO Secure Server Email Login
a. Use Strong Passwords: Encourage users to create strong, unique passwords for their email accounts and enable multi-factor authentication whenever possible.
b. Regularly Update Software: Keep your SSO provider, email server software, and email clients up to date with the latest security patches to protect against known vulnerabilities.
c. Monitor and Audit: Implement monitoring and auditing mechanisms to detect any suspicious activities or unauthorized access attempts. Regularly review logs and reports to identify potential security incidents.
d. Provide Security Awareness Training: Continuously educate users about email security, common phishing techniques, and how to identify and report suspicious emails or activities.
Conclusion
SSO Secure Server Email Login is a powerful solution for enhancing email security, simplifying user access, and protecting sensitive information. By implementing SSO and combining it with a secure server, you can significantly reduce the risk of data breaches and unauthorized access to your email communications. Make sure to choose a reliable SSO provider like Pure ID , follow best practices, and educate users about email security to maximize the effectiveness of your SSO secure server email login implementation. Stay proactive in safeguarding your email communications and enjoy the benefits of a secure and convenient email experience.
Power of Unified Endpoint Management Solutions
In today’s digital landscape, organizations are grappling with the management and security challenges posed by the proliferation of devices. From desktops and laptops to smartphones and tablets, the diverse array of endpoints can be overwhelming to control and protect. However, thanks to the advent of Unified Endpoint Management (UEM) solutions, businesses can now efficiently manage and secure their endpoints from a single, centralized platform. In this blog post, we will explore the benefits and features of UEM software and discuss how it can revolutionize device control and security in the modern enterprise.
Understanding Unified Endpoint Management Solutions
To begin our exploration, let’s define Unified Endpoint Management (UEM). UEM is a comprehensive approach to managing and securing all endpoints, including desktops, laptops, smartphones, tablets, and IoT devices, through a unified platform. It enables IT administrators to streamline device management tasks, such as software distribution, configuration, and updates, as well as enforce security policies across all endpoints, irrespective of their operating systems or locations.
Key Benefits of Unified Endpoint Management Software
2.1 Centralized Management:
UEM software provides a centralized console that offers a holistic view of all endpoints, allowing administrators to monitor, manage, and troubleshoot devices from a single interface. This streamlines IT operations, reduces administrative overhead, and improves efficiency.
2.2 Simplified Device Provisioning:
With UEM, IT teams can easily provision new devices by automating the setup process. Configuration settings, software installations, and security policies can be pre-defined and pushed to devices, ensuring consistency and reducing the time required for manual setup.
2.3 Enhanced Security:
UEM software plays a crucial role in safeguarding endpoints from potential threats. It allows administrators to enforce security policies, such as device encryption, password complexity, and application whitelisting, ensuring compliance and protecting sensitive data. Furthermore, UEM enables remote device lock and data wipe capabilities, enhancing data security in case of loss or theft.
2.4 Improved Productivity:
UEM software empowers end-users by providing them with a seamless experience across devices. Employees can access their data and applications from any endpoint, enabling flexible work arrangements and enhancing productivity. UEM also facilitates self-service options, empowering end-users to install approved applications or perform routine tasks without IT assistance.
Section 3: Key Features of Unified Endpoint Management Solutions
3.1 Device Inventory and Tracking:
UEM software offers comprehensive device inventory capabilities, allowing administrators to track and manage all endpoints within the organization. This includes information on hardware specifications, software installations, and device usage patterns, which assists in making informed decisions regarding resource allocation and device retirement.
3.2 Software Distribution and Patch Management:
UEM enables centralized software distribution, ensuring that devices are equipped with the latest applications and updates. It also facilitates patch management by automating the deployment of security patches and updates across all endpoints, reducing vulnerabilities and enhancing the overall security posture.
3.3 Mobile Device Management (MDM):
UEM software includes MDM functionalities that enable organizations to manage and secure mobile devices. It offers features like device enrollment, remote configuration, app management, and data protection, ensuring comprehensive control and security for smartphones and tablets.
3.4 Endpoint Compliance and Policy Enforcement:
UEM allows administrators to define and enforce security policies across all endpoints, ensuring compliance with regulatory requirements and internal standards. It provides real-time monitoring and alerts for policy violations, enabling proactive remediation to maintain a secure environment.
Which unified endpoint management solutions we offer?
SureMDM
With SureMDM we can develop a project solution that drives online revenues.
Surefox
We can develop a project solution that drives online revenues.
Surelock
We can develop a project solution that drives online revenues.
Astro Contacts
We can develop a project solution that drives online revenues.
Conclusion
Unified Endpoint Management (UEM) software is a game-changer for organizations seeking efficient device control and robust security. By centralizing device management, simplifying provisioning, enhancing security measures, and improving productivity, UEM software empowers businesses to navigate the complex endpoint landscape with ease. Embracing UEM can help organizations streamline operations, protect sensitive data, and unlock the full potential of their endpoints in the digital age. Invest in a reliable UEM solution today to elevate your device management and security capabilities to new heights. Contact us at GreenEdge Computers to know more.
Safeguarding Corporate Email Security: Keeping Your Emails Safe
In today’s digital world, email is an important way businesses communicate. But did you know that emails can be vulnerable to hackers and cyber threats? It’s crucial to protect your email from these risks. Let’s explore why email security is important and how Green Edge Computers can help keep your information safe.
Why is Email Security Important?
Emails often contain private information like passwords, financial details, and sensitive customer data. If not protected, hackers can steal this information or infect your computer with harmful viruses. By securing your email, you ensure the confidentiality of your communications and maintain trust with clients and partners.
Common Email Security Threats:
- Phishing Attacks: Some emails may look real but are actually scams trying to trick you into revealing personal information. They may ask for your passwords or financial details. Be cautious and double-check the email’s source before sharing any sensitive data.
- Malware and Ransomware: Attachments or links in emails can contain dangerous software that can harm your computer or even hold your files hostage. Avoid opening attachments or clicking on suspicious links to protect your device and data.
- Email Spoofing: Cybercriminals can pretend to be someone else by faking the sender’s email address. They might impersonate your bank or a trusted company to deceive you into sharing sensitive information. Be skeptical of unexpected emails asking for personal details.
Green Edge Computers’ Solutions for Secure Email:
Green Edge Computers understands the importance of email security and offers solutions to keep your information safe.
- Email Encryption: Green Edge Computers uses advanced encryption techniques to protect your email content. Encryption makes your emails unreadable to unauthorized individuals, ensuring that only the intended recipients can access them.
- Spam and Malware Filtering: To prevent malicious emails from reaching your inbox, Green Edge Computers employs filters that detect and block spam and harmful content. This reduces the risk of falling victim to phishing attempts or downloading harmful files.
- Two-Factor Authentication (2FA): Adding an extra layer of security, Green Edge Computers recommends enabling two-factor authentication. This means you need a second verification step, like a unique code sent to your phone, to access your email. It helps ensure that even if someone knows your password, they can’t access your account without the additional code.
- Employee Training: Green Edge Computers emphasizes the importance of educating employees about email security. They provide training to help recognize phishing attempts, suspicious attachments, and risky online behaviors. By educating your employees, you create a stronger defense against email threats.
Best Practices for Email Security:
Apart from Green Edge Computers’ solutions, here are some best practices to enhance your email security:
- Keep your software and devices updated with the latest security patches.
- Use strong passwords and avoid reusing them for different accounts.
- Think twice before clicking on links or opening attachments from unfamiliar sources.
- Regularly back up your email data to ensure you can recover it in case of any issues.
Conclusion:
Email security is crucial for businesses of all sizes. By implementing the solutions provided by Green Edge Computers and following best practices, you can protect your email from cyber threats. Safeguarding your email ensures the confidentiality of your communications, maintains trust, and keeps your sensitive information secure. Contact Us to know more about our service
Best Unified Endpoint Management Software
Unified Endpoint Management (UEM) is a comprehensive approach to managing and securing all endpoints in an organization’s network, including desktops, laptops, smartphones, tablets, and other connected devices. It provides a centralized platform for IT administrators to manage, monitor, and secure these endpoints, improving operational efficiency and enhancing security posture. In this blog post, we will explore the concept of UEM and discuss some of the best practices and solutions in the field.
What is Unified Endpoint Management (UEM)?
Unified Endpoint Management is an evolution of traditional endpoint management approaches that focus on individual device types, such as Sure Mobile Device Management (MDM) for mobile devices or Client Management Tools (CMT) for desktops and laptops. UEM consolidates these disparate management tools into a single platform, enabling organizations to streamline their management processes and gain better visibility and control over all their endpoints.
Implementing a UEM strategy offers several benefits for organizations, including:
Benefits of Unified Endpoint Management:
- Centralized Management: UEM provides a centralized console or dashboard that allows administrators to manage all endpoints from a single interface. This streamlines management tasks, reduces administrative overhead, and improves operational efficiency.
- Improved Security: UEM solutions enable organizations to enforce security policies, manage software updates, and implement data protection measures across all endpoints. This helps to mitigate security risks and ensures compliance with regulatory requirements.
- Enhanced Productivity: UEM allows for efficient software distribution, remote troubleshooting, and policy enforcement. It improves endpoint performance, reduces downtime, and increases end-user productivity.
- Flexibility and Scalability: UEM supports a wide range of endpoint types and operating systems, making it adaptable to diverse IT environments. It also provides scalability, allowing organizations to easily onboard new devices as their needs evolve.
- Cost Savings: By consolidating management tools and processes, UEM reduces the need for multiple licenses and minimizes administrative overhead. This can result in cost savings for organizations in the long run.
Key Features and Capabilities of UEM:
When evaluating UEM solutions, it’s essential to consider the following key features and capabilities:
- Device Enrollment and Provisioning: UEM solutions should provide easy and efficient ways to enroll and provision devices onto the management platform, supporting both corporate-owned and bring-your-own-device (BYOD) scenarios.
- Configuration and Policy Management: Administrators should be able to define and enforce security policies, device configurations, and software settings across all managed endpoints.
- Application Management: UEM should offer capabilities for managing the entire application lifecycle, including app distribution, updates, and removal, as well as support for both corporate and public app stores.
- Device Security and Compliance: UEM should provide robust security features, such as device encryption, remote lock/wipe, and threat detection. It should also facilitate compliance with regulatory standards and offer reporting and auditing capabilities.
- Patch and Update Management: UEM should allow organizations to efficiently distribute software updates and patches across all managed endpoints, ensuring they are up-to-date and protected against known vulnerabilities.
- Remote Support and Troubleshooting: UEM should enable IT administrators to remotely troubleshoot and support end-users by providing remote control capabilities, real-time monitoring, and remote assistance tools.
- Analytics and Reporting: UEM should offer comprehensive reporting and analytics features, providing insights into device performance, compliance status, and security posture.
Best Unified Endpoint Management Solutions:
There are several UEM solutions available in the market, each with its own set of features and capabilities. Here are a few top UEM solutions to consider:
- VMware Workspace ONE: Workspace ONE is a comprehensive UEM platform that combines device management, application management, and access control capabilities. It offers robust security features, and integration with VMware’s other solutions, and supports various operating systems and device types.
- Microsoft Endpoint Manager: Microsoft Endpoint Manager is a unified management platform that combines Microsoft Intune and Configuration Manager. It provides a single console to manage both traditional and modern devices, with features like policy enforcement, application management, and security controls.
- IBM Security MaaS360: MaaS360 is a cloud-based UEM solution that offers device management, application management, and security features. It provides a user-friendly interface, supports multiple platforms, and includes AI-driven insights for better decision-making.
- Cisco Meraki Systems Manager: Meraki Systems Manager is a cloud-based UEM solution that focuses on simplicity and ease of use. It offers device management, application deployment, and network security features, making it a suitable choice for organizations with distributed environments.
- Jamf Pro: Jamf Pro is a UEM solution specifically designed for managing Apple devices in enterprise environments. It provides comprehensive management capabilities for macOS, iOS, and iPadOS devices, including device enrollment, configuration, and security controls.
These are just a few examples of UEM solutions available in the market. When selecting a UEM solution, it’s important to consider your organization’s specific requirements, budget, and compatibility with existing infrastructure.
Conclusion:
Unified Endpoint Management is becoming increasingly important as organizations embrace diverse endpoint types and face growing security challenges. By adopting a UEM strategy and leveraging the right solution, organizations can achieve centralized management, improved security, and enhanced productivity across their entire endpoint landscape. Evaluate your organization’s needs, explore different UEM solutions, and implement a comprehensive approach to endpoint management to maximize the benefits and secure your digital assets effectively. Contact us at GreenEdge to know more…
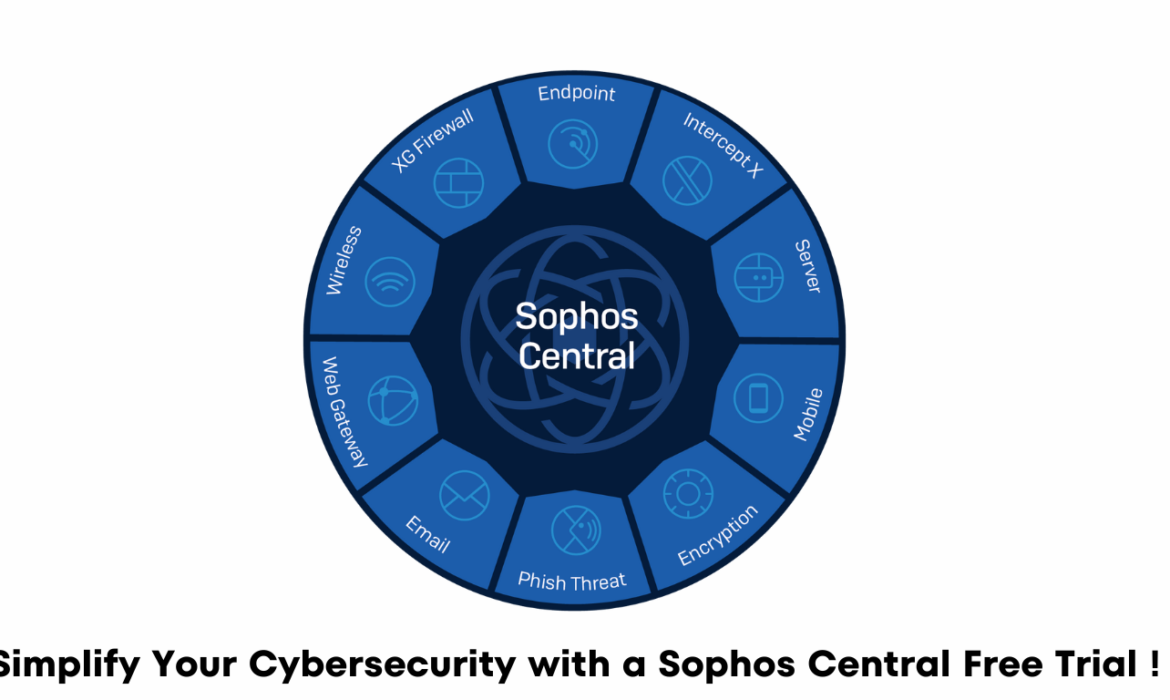
Simplify Your Cybersecurity with a Sophos Central Free Trial !
In today’s digital landscape, protecting your business from cyber threats is of utmost importance. With the ever-evolving nature of cyberattacks, having a robust and comprehensive cybersecurity solution is essential. Sophos Central, a leading cloud-based security platform, offers a suite of powerful tools to safeguard your organization’s digital assets. If you’re considering implementing Sophos Central for your business, you’re in luck! In this blog post, we’ll explore the benefits of Sophos Central and guide you on how to start with a free trial. Let’s dive in!
Why Sophos Central and how to get Sophos central free trial?
- Sophos Central stands out as a comprehensive and user-friendly cybersecurity platform that simplifies threat management for businesses of all sizes. Whether you’re an IT professional or a small business owner, Sophos Central offers an array of features designed to protect your systems and data. Here are a few reasons why Sophos Central is worth considering:
a. Centralized Management:
With Sophos Central, you can manage all your security solutions from a single, unified dashboard. This centralized approach allows for easier policy enforcement, streamlined updates, and better visibility across your organization’s security landscape.
b. Advanced Threat Protection:
Sophos Central combines cutting-edge technologies, such as deep learning and behavioral analysis, to identify and mitigate advanced threats in real-time. By leveraging artificial intelligence and machine learning, Sophos Central offers proactive defense against the latest malware, ransomware, and zero-day attacks.
c. Scalability and Flexibility:
Whether you have a small team or a large enterprise, Sophos Central scales to meet your business needs. As your organization grows, you can easily add or remove licenses and expand your security capabilities without disruption.
Getting Started with sophos central free trial:
- Embarking on a free trial of Sophos Central is a great way to experience its features firsthand and determine if it’s the right fit for your business. Follow these steps to kickstart your free trial:
a. Visit the Sophos Central Website:
Head over to the official Sophos Central website to begin your journey. Look for the “Free Trial” or “Start Free Trial” button, which should be prominently displayed on the homepage.
b. Sign Up for an Account:
Create a new account by providing your basic information, such as your name, email address, and company details. You may also need to select your desired product edition during this process.
c. Choose Your Security Solutions:
Sophos Central offers a range of security products, including endpoint protection, server protection, email security, and more. Select the solutions that align with your organization’s requirements.
d. Set Up Your Environment:
After choosing your desired security solutions, follow the on-screen instructions to configure your Sophos Central environment. You may need to install agents on your endpoints or make necessary network adjustments, depending on the selected solutions.
e. Explore and Evaluate:
Once your environment is set up, take the time to explore the features and functionalities of Sophos Central. Test its performance, assess its user-friendliness, and evaluate its ability to protect your systems and data.
f. Reach Out for Assistance:
During your free trial, if you encounter any issues or have questions, Sophos offers excellent customer support. Take advantage of their resources, including documentation, knowledge base, and contact options, to ensure a smooth trial experience.
Moving Forward with Sophos Central:
- After thoroughly assessing Sophos Central during your free trial, you’ll have a better understanding of its value for your organization. If you decide to continue using Sophos Central, you can seamlessly transition from the trial version to a paid subscription. Sophos offers various licensing options and packages tailored to meet the diverse needs of businesses.
Conclusion:
Sophos Central’s comprehensive security features, centralized management, and advanced threat protection make it an ideal choice for organizations seeking robust cybersecurity solutions. By starting with a free trial, you can experience firsthand the benefits and capabilities of Sophos Central. Don’t compromise your business’s security—take advantage of Sophos Central and protect your digital assets effectively. Get started with sophos central free trial today and experience the power of next-generation cybersecurity!
Enhancing Cybersecurity with Mimecast Web Security
In today’s digital landscape, ensuring robust cybersecurity measures is crucial for individuals and organizations alike. One area that demands particular attention is web security. With the ever-growing threat of cyberattacks, companies need reliable solutions to protect their sensitive data and systems. Mimecast Web Security emerges as a comprehensive and effective solution to safeguard against web-based threats. In this blog, we will explore the features, benefits, and implementation of Mimecast Web Security, shedding light on its importance in the realm of cybersecurity.
Understanding Mimecast Web Security:
Mimecast Security is a cloud-based web security solution designed to defend against various cyber threats, including malware, ransomware, phishing attacks, and data loss. By providing comprehensive web protection, it enables organizations to prevent unauthorized access, block malicious websites, and enforce acceptable use policies. With its advanced threat intelligence and real-time scanning capabilities, Mimecast offers a robust defense mechanism against evolving cyber threats.
Key Features and Capabilities:
- URL Filtering: Mimecast Security employs a powerful URL filtering feature that identifies and blocks access to malicious or inappropriate websites, preventing employees from inadvertently visiting harmful web pages.
- Advanced Threat Protection: With a combination of advanced threat intelligence, sandboxing, and machine learning, Mimecast detects and blocks sophisticated threats like zero-day attacks, spear-phishing, and drive-by downloads.
- Data Loss Prevention (DLP): Mimecast’s DLP capabilities help prevent sensitive data leakage by monitoring web-based communications and enforcing policies to safeguard valuable information.
- Cloud-Based Deployment: As a cloud-based solution, Mimecast Security offers seamless implementation and scalability, ensuring consistent protection across multiple devices and locations.
Benefits of Mimecast Security:
- Enhanced Web Protection: By actively monitoring web traffic, Mimecast prevents access to malicious websites and ensures a safe browsing experience for employees, reducing the risk of malware infections and data breaches.
- Simplified Management: With its intuitive management console, Mimecast provides easy administration and centralized control over web security policies, allowing organizations to streamline their cybersecurity efforts.
- Regulatory Compliance: Mimecast Web Security helps organizations meet regulatory requirements by enforcing policies that protect sensitive data and prevent unauthorized access or data loss.
- Proactive Threat Intelligence: Leveraging Mimecast’s extensive threat intelligence network, the solution stays updated with the latest security threats and adapts to new attack vectors, ensuring proactive defense against emerging cyber risks.
Implementing Mimecast Security:
- Integrating Mimecast Security into your organization’s cybersecurity framework is a straightforward process:
- Assess your security needs and identify the areas where web security is crucial.
- Work with Mimecast experts to define the deployment strategy and establish appropriate policies.
- Deploy the Mimecast Web Security solution and configure it according to your organization’s requirements.
- Train employees on safe browsing practices and educate them about the benefits and functionalities of Mimecast Web Security.
- Regularly monitor and update security policies and configurations to adapt to changing threats.
Conclusion:
Mimecast Web Security offers a comprehensive approach to web protection, empowering organizations to mitigate the risks associated with web-based cyber threats. By leveraging its advanced features and capabilities, businesses can safeguard their valuable data, enhance productivity, and maintain a secure digital environment. Investing in Mimecast is a proactive step towards fortifying your organization’s cybersecurity posture and ensuring a resilient defense against evolving threats in the digital landscape. Contact us at Green Edge Computers to know more.
All you need to know about Ransomware attacks
Ransomware attacks have become increasingly common in recent years, and they can have devastating effects on both individuals and organizations. One of the most important things to know about ransomware is that paying the ransom is never a guarantee that your data will be restored. In this blog post, we’ll take a closer look at ransomware data recovery, and what you can do if you find yourself the victim of a ransomware attack.
What is ransomware?
Ransomware is a type of malware that encrypts a victim’s files and demands payment in exchange for the decryption key. Ransomware can be spread through phishing emails, compromised websites, and other means. Once ransomware infects a system, it can quickly spread to other systems on the same network, making it difficult to contain.
Why paying the ransom may not be the best option?
While it may be tempting to pay the ransom to get your data back, doing so is never a guarantee that your data will be restored. There have been cases where victims paid the ransom, only to find that their data was still unrecoverable. Additionally, paying the ransom only encourages the attackers to continue their malicious activities.
Ransomware data recovery options
If you’ve been the victim of a ransomware attack, there are a few options for data recovery. The first step is to disconnect the infected device from the network to prevent further spread of the malware. Next, you can try to restore your files from a backup. It’s important to have regular backups in place so that you can easily recover your data in the event of an attack.
If you don’t have a backup, you may be able to use a data recovery tool to restore your files. These tools work by scanning the hard drive for traces of the original files and attempting to reconstruct them. However, there’s no guarantee that these tools will be successful, especially if the ransomware has overwritten the original files.
Finally, if all else fails, you may need to seek the help of a professional data recovery service. These services specialize in recovering data from damaged or corrupted devices, and they may be able to help you recover your files even if they’ve been encrypted by ransomware.
Preventing future ransomware attacks
The best way to deal with ransomware is to prevent it from happening in the first place. Here are a few tips to help you protect your data from ransomware attacks:
- Keep your operating system and software up to date with the latest security patches
- Use a reputable antivirus program and keep it updated
- Be cautious when opening email attachments or clicking on links
- Use strong, unique passwords for all your accounts
- Regularly backup your data to an external hard drive or cloud storage service
How can we help?
We have the best solutions for Endpoint Protection of your business. Some of them are following:
Sophos
Unified Endpoint Management
42Gears
SureMDM
SureFox
SureLock
Astro Contacts
Conclusion
In conclusion, ransomware attacks can be devastating, but there are ways to recover your data without paying the ransom. By following the tips above, you can protect yourself from future attacks and keep your data safe.
Ransomware attacks have become increasingly common in recent years, and they can have devastating effects on both individuals and organizations. One of the most important things to know about ransomware is that paying the ransom is never a guarantee that your data will be restored. In this blog post, we’ll take a closer look at ransomware data recovery, and what you can do if you find yourself the victim of a ransomware attacks. Contact us at Green Edge Computers to know more.
Importance of Sophos Network Firewall Security
The introduction provides an overview of why network firewall security is important for businesses, but let’s expand on this a bit. Cyber threats are becoming more sophisticated and frequent, and businesses of all sizes are at risk. Small businesses are often targeted by cybercriminals because they are perceived as being easier to hack. A data breach can result in significant financial losses, not to mention damage to a business’s reputation. Implementing network firewall security is an essential step in protecting your business from these threats.
What is Network Firewall Security?
The article briefly describes what network firewall security is, but let’s provide a bit more detail. Sophos network firewall is a system of hardware or software devices that monitor and control traffic between your internal network and the internet. It acts as a barrier, allowing authorized traffic in and out while blocking any traffic that is not authorized. Firewalls can be configured to block traffic based on IP address, protocol, port, or application. There are several types of firewalls, including packet-filtering firewalls, stateful inspection firewalls, and application-level gateways.
Why is Network Firewall Security Important?
The article provides a few reasons why Sophos network firewall security is important, but let’s expand on this a bit further. In addition to the financial and reputational damage that can result from a data breach, businesses can also face legal and regulatory consequences. For example, many countries have data protection laws that require businesses to take steps to protect personal information. Failing to do so can result in fines and legal action. Additionally, businesses that rely on intellectual property can be at risk of theft or espionage. Implementing network firewall security is one way to mitigate these risks and protect your business assets.
What is Sophos Firewall?
Sophos Firewall is a hardware-based network security solution that uses advanced threat detection and prevention capabilities, including artificial intelligence and machine learning, to protect against cyber threats. It includes intrusion prevention, application control, web filtering, VPN capabilities, and integrated web application firewall and email security features. It is an effective and user-friendly solution for businesses of all sizes looking to enhance their cybersecurity posture.
How to Implement Network Firewall Security Effectively?
The article provides some general steps for implementing network firewall security, but let’s provide a bit more detail on each step.
- Choose the Right Firewall: There are several factors to consider when choosing a firewall, including the size of your network, the types of traffic you need to allow, and your budget. Hardware-based firewalls are typically more expensive but offer better performance, while software-based firewalls are more affordable but may not be as powerful. It’s important to choose a firewall that meets your business needs and provides the level of protection you require.
- Define Your Network Policy: Before implementing a firewall, you’ll need to define your network policy. This involves deciding which traffic should be allowed and which should be blocked. For example, you may want to block all incoming traffic except for traffic on specific ports, such as port 80 for web traffic. You’ll also need to set up access control lists to determine who has access to your network and what they can do.
- Regularly Update Your Firewall: Cyber threats are constantly evolving, so it’s essential to keep your firewall up to date with the latest security patches and updates. Many firewalls include automatic update features, but it’s important to ensure that these are enabled and working correctly.
- Educate Your Employees: Your employees can be a weak link in your network security, so it’s important to educate them about the importance of network security and best practices. This includes using strong passwords, avoiding suspicious emails or websites, and reporting any security incidents or concerns to the IT department.
Conclusion:
The conclusion provides a summary of the key points made in the article, but let’s expand on this a bit. Implementing Sophos network firewall security is an important step in protecting your business from cyber threats. In addition to the steps outlined in the article, there are several other best practices to consider, such as implementing multi-factor authentication, conducting regular security audits, implementing multi-factor authentication, conducting regular security audits, and regularly backing up your data to protect against data loss.
By taking these steps and staying vigilant, you can help protect your business from cyber threats and ensure the safety of your valuable data and assets. Remember, network security is an ongoing process, and it’s important to stay informed and up to date on the latest threats and best practices. A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Green Edge Computers provide you with the best Sophos network protection software Firewall. Contact Us Now.
Sophos Firewall for network security
In the present-day virtual age, firewall for network security have grown to be more crucial than ever before. With the upward thrust of cyber-assaults and statistics breaches, ensuring that your organization’s network is steady and guarded against capability threats is vital. Imposing a firewall is one of the most effective ways to gain that.
Sophos firewall is a community protection system that video displays units and controls incoming and outgoing site visitors based on predefined security regulations. It acts as a barrier between an agency’s inner community and the net, supporting to save you unauthorized access to and attacks from external resources.
How does Sophos Firewall for network security Work?
Firewalls work by examining incoming and outgoing network site visitors and permitting or blocking them primarily based on a set of predefined rules.
There are 3 fundamental varieties of firewalls:
- packet filtering.
- Stateful inspection.
- Proxy provider.
Packet filtering firewalls have a look at the header information of every packet of records that enters or leaves the network and examine it to a set of predefined rules. If the packet meets the standards, it is allowed to skip via, and if it does now not, it’s miles blocked.
Stateful inspection firewalls cross one step in addition to analyzing not longer most effective the header but also the contents of each packet. This sort of firewall continues a document of the connections among the inner and external networks, allowing it to understand and filter out doubtlessly harmful site visitors.
Proxy service firewalls act as intermediaries between the inner and outside networks, receiving and forwarding traffic on behalf of the users. This form of firewall can offer extra protection capabilities, such as content filtering and malware scanning.
Types of Firewalls
We can categorize firewalls into three main types: hardware-based, software-based, and cloud-based.
Hardware-based firewalls are physical gadgets which might be installed at the network perimeter to display and manipulate community visitors. They provide excessive degrees of overall performance and may be without difficulty managed and configured.
Software-based firewalls, on the other hand, are established on man or woman gadgets including servers, computer systems, and laptops. They shield the device’s degree, making them perfect for cell gadgets and far-off workers.
Cloud-based totally firewalls are a more modern type of firewall that is introduced as a provider over the net. They are relatively scalable and may be easily deployed across more than one place, making them perfect for businesses with distributed workforces.
Benefits of Sophos Firewalls
Firewalls offer several blessings for network safety, along with:
Limitations of Firewalls
- Protection against cyber assaults: Firewalls can help save you from unauthorized access, malware infections, and different types of cyber assaults using blockading malicious visitors.
- Control over community visitors: Firewalls allow organizations to control and manipulate the float of network traffic, ensuring that the best-authorized customers and programs have to get right of entry to community sources.
- Increased privacy and confidentiality: Firewalls can assist to guard touchy records and make certain that it isn’t intercepted or accessed with the aid of unauthorized events.
- Compliance with regulatory necessities: Many industries and organizations are in situations with regulatory necessities, along with HIPAA or PCI-DSS, which require the implementation of particular security measures. Firewalls can help make sure compliance with these rules by way of presenting a critical layer of security.
While Sophos firewalls are a vital aspect of network security, they do have some barriers:
- Inability to defend against all styles of attacks: Firewalls are designed to protect towards specific forms of threats, consisting of malware and unauthorized entry. However, they will now not be powerful against extra superior threats, consisting of zero-day assaults or targeted assaults.
- Difficulty in detecting and blocking off malicious traffic: Hackers can use diverse techniques to skip firewalls, such as disguising their site visitors as legitimate site visitors or the usage of encryption. Firewalls might not be able to come across or block this sort of malicious site visitor.
- The complexity of configuration and management: Firewalls may be complicated to configure and manage, requiring specialized expertise and understanding. Improper configuration can result in false positives or false negatives, that can impact network performance and protection.
Best Practices for Firewall Implementation
To maximize the advantages of firewalls and limit their obstacles, it’s far vital to observe satisfactory practices for implementation, which include:
- Regular updates and patches: Firewalls ought to be updated frequently to make certain that they’re blanketed against state-of-the-art threats and vulnerabilities.
- Proper configuration and trying out: Firewalls need to be configured and examined to make sure that they may be blockading malicious site visitors and permitting legal traffic. This includes putting in place guidelines and rules that replicate the employer’s safety requirements.
- Monitoring and analysis of network site visitors: Firewalls must be monitored and analyzed often to discover potential threats and vulnerabilities. This includes reading logs and signals generated through the firewall and accomplishing regular protection tests.
- Employee schooling and cognizance: Employees ought to be taught the significance of community safety and the position of firewalls in protection in opposition to cyber threats. This consists of teaching employees the way to perceive and record capacity protection incidents.
Conclusion
In the end, firewalls are a critical element of network protection and firewall for network security play an essential role in defensive organizational property from cyber threats. By imposing firewalls and following quality practices for configuration and management, agencies can considerably improve their community protection posture. However, it’s essential to recognize the restrictions of firewalls and enforce additional security measures to address extra advanced threats. As generation continues to evolve, firewalls will possibly continue to be a crucial thing of network security, and organizations will want to live knowledgeably and adapt to new threats and vulnerabilities.
Five Effective Ways to Prevent Data Loss with Safetica
Data loss may be a nightmare for individuals and groups alike. Whether it is a hardware failure, a cyberattack, or human mistakes, losing important facts may have critical results. Fortunately, there are numerous techniques you may use to prevent data loss and shield your valuable facts.
Regularly Back Up Your Data
One of the most essential approaches to prevent information loss is to lower back up your records regularly. Backing up your statistics is developing a copy of your documents and store it in a separate location. This can be carried out using lots of techniques, consisting of cloud-primarily based backups, external hard drives, and community-attached garage (NAS). By backing up your records frequently, you could ensure that you have a copy of your critical files in case of facts loss.
There are unique methods to backup your facts:
- Cloud-Based Backups: Cloud storage offerings like Google Drive, Dropbox, and OneDrive offer a handy and dependable way to again up your facts. These offerings mechanically sync your files to the cloud, ensuring that you constantly have an up-to-date backup of your statistics.
- External Hard Drives: External difficult drives are a low-priced and powerful way to return your records. Simply connect the force to your pc and use a backup software program to create a duplicate of your files. External tough drives are portable, so you can take them with you in case of an emergency.
- Network Attached Storage (NAS): NAS devices are essentially small servers which are designed for document storage and sharing. They may be used to return your facts, and they offer the delivered benefit of being handy from everywhere with a web connection.
Use Antivirus and Firewall Software
Malware and viruses can purpose serious damage to your device and facts, so it is critical to guard your devices against malicious attacks. Antivirus software programs will experiment your system for viruses and malware, even as firewall software will block unauthorized access to your community and gadgets. By using antivirus and firewall software programs, you may substantially reduce the hazard of records loss due to cyberattacks.
Here are some hints for deciding on antivirus and firewall software programs:
- Choose a reputable supplier: Make sure the vendor you pick out has awesome recognition for presenting reliable and powerful antivirus and firewall software.
- Look for actual-time safety: Real-time protection means the software will test for viruses and malware in actual time as you use your laptop.
- Consider a complete safety suite: A complete protection suite will encompass antivirus, firewall, and different security functions in a single bundle.
Best Solution for Data Loss Prevention:
Safetica Nxt
Safetica Data Discovery
Safetica protects your sensitive/ confidential data from frauds in this hybrid work era by quickly detecting security risks on endpoints and stopping incidents from day one.
Implement Data Access Controls
Human blunders are one of the maximum not unusual reasons for records loss, so it is critical to restrict the right of entry to sensitive data to the handiest individuals who need it. This can be achieved through information getting right of entry to controls, which encompass using strong passwords, frequently converting passwords, and limiting access to touchy records to only those who need it. By implementing information entry to controls, you could drastically lessen the danger of information loss due to human errors.
Here are some pointers for implementing facts access controls:
- Use sturdy passwords: Use passwords which might be tough to bet and consist of a mixture of letters, numbers, and special characters.
- Regularly exchange passwords: Change your passwords frequently to make sure that they continue to be steady.
- Limit get admission to touchy information: Only provide admission to sensitive information to individuals who want it to carry out their task responsibilities.
Train Employees on Data Security Best Practices
Employees are regularly the weakest link in records security, so it is critical to teach them statistics security best practices. This consists of teaching them the way to recognize phishing scams, the way to create sturdy passwords, and the way to securely cope with touchy records. By schooling your personnel on information safety quality practices, you could ensure that they cope with statistics securely and reduce the chance of records loss.
Creating a powerful information protection training application:
- Make it mandatory: Make information protection education obligatory for all employees, irrespective of their function.
- Include actual-global examples: Use actual-world examples to assist personnel understand the consequences of data breaches and the way to save them.
- Provide ongoing education: Offer ongoing schooling to make sure that employees live updated with the trendy statistics and safety satisfactory practices.
- Monitor and implement compliance: Monitor worker compliance with statistics safety rules and enforce consequences for noncompliance.
Invest in Data Recovery Services
Despite your nice efforts to prevent statistics loss, it is nonetheless viable that you can revel in a facts loss occasion. That’s why it is critical to put money into records recovery offerings to help you recover your lost information speedy and effectively. Data recovery services let you recover records from loads of resources, including hard drives, flash drives, and even smartphones.
Here are some suggestions for deciding on a data recovery carrier:
- Choose a reputable company: Make positive the statistics recovery company you pick has good popularity for imparting reliable and effective information restoration services.
- Check their achievement fee: Ask about their fulfilment price for getting better-misplaced facts, and make sure it’s consistent with enterprise standards.
- Ask approximately their records privacy policy: Make positive the records recuperation issuer has a strict statistics privacy policy to ensure that your information stays secure.
Conclusion
In this blog, we have discussed Five Effective Ways to Prevent Data Loss. Data loss may have serious outcomes, you may substantially lessen the chance of facts loss and defend your valuable statistics. Regularly backing up your information, the usage of antivirus and firewall software programs, implementing facts get right of entry to controls, schooling personnel on records security, nice practices, and investing in facts healing services can help make sure that your records stay secure and steady. Remember, prevention is the exceptional defence against information loss, so start imposing those techniques these days to protect your valuable facts.