Best practices for Endpoint Security
If you think we do not need to secure your endpoints then you are wrong because corporate endpoints are the main target and entry point of cyber attackers or data breaches. Securing your endpoints is very important because every year 17% of data breaches and cyber-attacks happen through endpoints.
Practices for endpoint security with the software by Sophos, it will help you to protect your endpoints. If you do not know about endpoint security practices and the importance of endpoint security. Then do not worry, in this article, we will share with you all the important information related to endpoint security.
What is endpoint security?
Before knowing the importance of endpoint security you should know what endpoint security is. Endpoint security helps you to protect your endpoint from cyber attackers and malicious actors. It helps you to secure endpoints and entry points on all devices such as desktops, mobile devices, and laptops.
Here, we shared with you a brief information about What endpoint security is. Now, we are going to share with you the importance of endpoint security.
Importance of Endpoint Security
Most people do not know the importance of endpoint security. Endpoint security is very important because of remote work. Remote workers’ devices are less protected and cyber attackers easily steal your data through remote workers’ devices. But endpoint security solutions help you to protect your devices. With the help of endpoint security, you can easily install a security solution on all remote workers’ devices.
It helps you to protect your computer from cyberattackers, ransomware, malware attacks, and phishing attacks.
Now, we are going to share with you best practices for endpoint security
Practices for endpoint security
Deploy Anti-Phishing Solutions
Phishing is the most common way for cyber attackers to steal your business information. Many cyber attackers start with phishing attacks. If you deploy anti-phishing solutions then you can easily protect your endpoints and decrease the level of malware, and cyber attack risk.
Protect Against Ransomware
This is the second best practice for endpoint security. Every business knows ransomware is the most dangerous and expensive cyber attack.
Endpoint security solutions help you to protect your system against ransomware attacks before they can steal or encrypt your all data and files.
Leverage Content Disarm and Reconstruction (CDR)
The potential for malicious content can leave businesses making a tradeoff between employee productivity and protection. Deploying CDR (Content Disarm and Reconstruction) helps you to eliminate this tradeoff by stripping malicious content from files before forwarding it to its intended recipient.
Defend Against Malicious Bots
This is one of the best endpoint security practices. Deploying anti-malicious bot protection for endpoints helps you to protect your endpoints and data from malicious bots and it also helps you to eliminate automated threats.
Automate Post-Breach Actions
After a data breach, the cost & impact to a company is determined by how quickly the organization can detect and respond to the cyber attack.
With the help of automating incident response on endpoints, you can enable an organization to minimize the cyber attackers’ access and ability to destroy.
Use endpoint security software
Endpoint security software helps you to protect entry points and all important corporate endpoints on all devices such as mobile, desktop, and laptops. Green Edge cOmputers provide you with the best endpoint security software. Contact us to get the best security software. Because your data is our responsibility.
Conclusion:
At Green Edge Computers, we are proud to offer comprehensive Best practices for Endpoint Security solutions powered by Sophos, a leading name in the cybersecurity industry. With the ever-evolving threat landscape, protecting your business’s endpoints is crucial in safeguarding sensitive data and ensuring the continuity of your operations. Our partnership with Sophos allows us to deliver top-notch security measures tailored to meet the unique needs of your organization. Contact us to know more.
How to protect against malware attacks?
Use secure authentication methods:
Using secure authentication methods help you to keep your data safe and secure. Always use strong and tricky passwords rather than using easy and simple passwords. Also, take two-factor authentication. If hackers steal your passwords, two-factor authentication is still there to protect your data.
Use administrator accounts only when necessary:
Malware is a type of software that can harm your computer. It can do a lot of bad things if it gets access to your computer, like stealing your personal information or damaging your files.
To protect yourself from malware, you should use Safetica Nxt. It is one of the best software for protecting from malware attacks. You should also avoid using the most powerful parts of your computer, which are usually reserved for people who have special access. Only use those powerful parts when you need to make important changes to your computer.
If you want to install new software on your computer, you should be very careful. Only install software that you know is safe and secure. And when you do install new software, make sure you use your special access only when you need to.
Green Edge Computers provides you with the best cybersecurity software Datto that helps you to keep your data safe.
Keep software updated:
No software is completely safe from malware, but software companies regularly release updates to fix any new security problems. To keep your computer safe, it’s important to regularly update your operating system, software programs, web browsers, and any add-ons you use. You should also regularly check your computer’s log reports for signs of malware and make sure all your software is up-to-date. By doing this, you can help protect your computer from harmful viruses and malware.
We provide you with the best data security software. For more information about Datto, you can call us at +97143323352.
Implement email security and spam protection:
Email is an important way for businesses to communicate, but it can also be a way for viruses and other harmful software to get onto your computer access and data. To reduce the chances of this happening, you should do a few things:
- Make sure you scan all emails you receive, including any attachments, to check for viruses before you open them.
- Use spam filters to stop unwanted or suspicious emails from getting into your inbox.
- Only click on links and open emails from sources that you know and trust. Don’t click on links or download files from unknown sources.
Here, we shared with you the top 5 ways. If you implement these ways regularly then malware has not dared to steal your data and information. Now, we are going to share with you the types of malware.
Types of malware attacks
Several types of malware attacks can harm your computer and steal your data. Here are some common ones:
- Virus: A virus is a basic type of malicious software that infects other programs or files and spreads from one computer to another. It can damage all your files, slow down your computer and steal your data.
- Trojan horse: A Trojan horse is a program that appears to be legitimate but contains malware. It can be used to steal your personal information, like your passwords or credit card details, and can also cause damage to your computer.
- Ransomware: It is the most dangerous and famous type of malware. You already heard about this. Ransomware is a type of malware that locks your computer or encrypts your files, making them inaccessible until you pay a ransom to the attacker. It can be very damaging and can result in permanent loss of data.
It’s important to protect your computer from these types of malware attacks by using anti-virus software, keeping your software up-to-date, and being cautious when opening emails or downloading files from the internet.
Conclusion
After reading this article, we hope now you understand how to protect against malware attacks. Safetica Nxt is the best software for protecting from online malware attacks. If you still have any questions or you want to get the best cyber security against malware then contact us at +97143323352. We feel happy to help you.
How Internet Security Firewalls Keep You Safe Online?
If you want to protect your data without any hassle then you should know about the firewalls. Implementing firewalls in your system is the best way to reduce cyber attacks. But if you do not know about internet security firewalls then do not worry in this article, we will share with you the complete information about firewalls such as the importance of firewalls, what are firewalls, and their advantages, and disadvantages of firewalls.
What is a Firewall?
An internet security firewall is a network security system that helps you to protect your data from external threats, external networks, and unauthorized access.
· Firewalls help you to filter your data by using the many defined policies and rules. That helps you to restrict suspicious data.
· A firewall works like a gatekeeper and it helps you to monitor and control incoming and outgoing network traffic.
· Any specific traffic, in the form of access requests, and requests for business data, to a resource behind the firewall security and inside the trusted network, will be inspected, analyzed & is allowed to pass or be blocked based on predefined security rules, and policies.
· The firewall security rules and policies are configured into the firewall & are customizable.
Importance of using Sophos firewalls
Using sophos firewall protection is very beneficial for your business. Here, we shared with you some important points that explain to you the importance of using firewalls:
Feature-1 :
Monitoring Network Traffic
Firewall protection starts with the monitoring of network traffic which helps you to keep your system protected. Monitoring of network traffic has many security measures that we describe in down below:
Source or destination-based blocking of incoming network traffic
This is one of the best and most common features of firewalls. This feature of the firewall helps you to block incoming traffic by looking at the source or destination of the traffic.
Block network traffic based on content –
This is the second most famous feature of firewalls. Did you know? Firewalls also help to prevent your important business files from viruses.
Here, we shared with you the two main features of using firewalls. Now, we are going to share with you the advantages and disadvantages of firewalls.
Advantages and Disadvantages of Firewall
Firewall security provides you with many benefits but it also has some disadvantages that we are going to describe in this section.
Advantages: Firewalls help you to handle all external threats and prevent your business. Using a firewall is an effective way to control threats and cyber attacks.
Disadvantages: The disadvantage of firewalls is that firewalls are not able to protect your data from internal threats, virus attacks, and authentication mechanisms.
There, we share with you the both merits and demerits. It’s up to you and your business whether you want an internet security firewall or not. For more information about firewalls contact us at Green Edge Computers.
Conclusion:
In conclusion,Sophos Firewall security is one of the best ways to prevent your data from external threats. In the above article, we share with you all the information related to the firewall. If you still have any questions or queries then you can read our other article or you can contact us at +971 43323352. We feel happy to help you!
Understanding Web Security Attacks: Safeguarding Your Digital Presence
In today’s digital world, web security attacks can put our personal information and online presence at risk. It’s essential to be aware of these threats and take steps to safeguard ourselves. In this blog, we’ll explore common web security attacks, understand their impact, and also discuss simple measures you can take to protect yourself online.
Cross-Site Scripting (XSS):
Cross-Site Scripting involves attackers sneaking harmful code into websites, which can then affect users who visit those sites. It can lead to stolen information or changes to the website’s content. To protect against XSS attacks, be cautious of unfamiliar websites. Also, ensure that your browser and antivirus software is up to date, and avoid clicking on suspicious links.
SQL Injection:
SQL Injection attacks happen when attackers manipulate a website’s database to gain unauthorized access or manipulate data. To prevent SQL Injection, avoid sharing sensitive information on untrusted websites, ensure the websites you use are reputable, and regularly update your software and applications.
Distributed Denial of Service (DDoS):
DDoS attacks aim to overwhelm websites or networks with excessive traffic, making them unavailable to users. To defend against DDoS attacks, rely on strong and reputable web hosting services, use content delivery networks (CDNs) to distribute traffic, and consider implementing firewall protection.
Cross-Site Request Forgery (CSRF):
CSRF attacks use suspicious emails and links to enter your system. The website may be a normal website. To prevent CSRF attacks, be cautious when clicking on links in emails or messages, verify the authenticity of websites before providing sensitive information, and regularly update your passwords.
Phishing Attacks:
Phishing attacks involve fake emails or websites that appear trustworthy, aiming to trick users into revealing personal information. To protect against phishing, be cautious of emails asking for sensitive information, avoid clicking on suspicious links, and verify the legitimacy of websites before entering any personal details.
Malware Infections:
Malware is a set of viruses that can affect your system and can also enter into your system. It can also steal your private information. To prevent malware infections, use reputable antivirus software. Also, avoid downloading files from unfamiliar sources, and regularly update your software and applications.
Daato to secure yourself from web security attacks
One effective solution to enhance your web security and protect yourself from various attacks is by utilizing Daato software. Daato offers robust features and tools designed to fortify your defenses against web security threats. Here’s how Daato can help secure your online presence:
- Advanced Threat Detection
- Web Application Firewall (WAF)
- Secure Authentication and Access
- Controls access to sensitive information.
- Regular Vulnerability Scanning
- Security Incident Response
By utilizing Daato software, you can significantly enhance your web security posture. Its advanced threat detection, real-time alerts, web application firewall, secure authentication, vulnerability scanning, and incident response capabilities work together to safeguard your systems and data from web security attacks. Invest in Daato to proactively protect your online presence and maintain a robust defense against evolving threats.
Conclusion:
Web security attacks are a real threat, but you protect yourself from this by using Datto a software made to secure you from online attacks. Contact us for more information regarding web security or network security. Stay vigilant, and be cautious of suspicious links or emails. Keep your software up to date, and use reputable websites and antivirus software.
SSO Secure Server Email Login: Keeping Your Emails Safe and Secure
In today’s digital world, sending emails is a common way to communicate with friends, family, and even businesses. But you are also aware about sometimes emails are also unsafe? That’s why it’s important to have a Secure Server Email Login. It provides you with extra safety while sending and receiving emails. In this blog, we’ll explain why Secure Server Email Login is important and how it works to protect you.
Why is SSO Secure Server Email Login important?
Just imagine you have a habit of writing a diary and you write everything on it like your passwords and all your details. And you also do not want that any reader can read this. That’s why you need an SSO Secure Server Email Login.
When you have a Secure Server Email Login, it means you have a special key to unlock your email account. This key is having a unique password that only you know. It’s like having a secret code that keeps your emails safe and secure. Without this key, no one can able to open your email.
How does SSO Secure Server Email Login work?
Let’s know how to secure server email login works:
Strong Passwords:
- When you create an email account remember to create a strong password. A strong password contains letters in upper case and the lower case also contains numbers and special characters. If you create a strong password it is hard to guess and break.
Two-Factor Authentication (2FA):
Two-Factor Authentication also plays an important role in providing you extra safety. When you try to login into your email there is an extra message that is sent to your message for login you need to enter that message code with your password. It provides you with extra safety.
Encryption:
Encryption is like turning your emails into secret codes that only the intended recipient can understand. When you send an encrypted email, it gets scrambled into a jumble of letters and numbers. Only the person with the right key can unscramble it and read your message. This ensures that even if someone intercepts your email, they won’t be able to understand what it says.
Protection against Phishing:
Phishing is a trick used by hackers and scammers to steal your information. They try to enter your system by sending you suspicious emails that may contain malware.
Regular Updates:
Just like you update your favorite video game to fix bugs and make it better, your email provider updates their system too. These updates often include important security improvements to keep your email account safe. It’s a good idea to keep your email client software and devices up to date so you can benefit from these security enhancements.
By using Secure Server Email Login, you can keep your emails safe from hackers and protect your personal information. It’s like having a virtual security guard watching over your email account.
Also remember to create a strong password, enable Two-Factor Authentication if available, be cautious of suspicious emails, and keep your software up to date. These simple steps will help you stay safe and enjoy the benefits of email communication.
Conclusion:
In conclusion, having a Secure Server Email Login is crucial for protecting your private information and keeping your emails secure.
We at Green Edge Computers provide you with the best SSO secure server services. We also provide you with all the safeties that you need for your business. Contact us to know more about our services.
SSO Secure Server Email Login: Guide to Secure Your Emails
In today’s digital world, email has become an integral part of our personal and professional lives. With the increasing risk of cyber threats, securing our email communications is of utmost importance. Single Sign-On (SSO) combined with a secure server is an effective solution to enhance email security and protect sensitive information. In this blog post, we will explore the concept of SSO Secure Server Email Login and discuss its benefits and implementation.
Understanding SSO and Secure Server Email Login
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications or websites with a single set of login credentials. It eliminates the need for multiple usernames and passwords, making the login process more convenient and user-friendly. A secure server email login ensures that the email communication between the server and the user remains encrypted and protected from unauthorized access.
Importance of Secure Email Communications
Emails often contain sensitive information, including personal details, financial data, or confidential business communications. Without proper security measures, these emails are vulnerable to interception, data breaches, or unauthorized access. By implementing SSO combined with a secure server email login, you can significantly reduce the risk of data leaks, identity theft, and other cyber threats.
Benefits of SSO Secure Server Email Login
a. Enhanced Security: SSO adds an extra layer of security by implementing robust authentication mechanisms, such as multi-factor authentication (MFA) or biometrics. Combining SSO with a secure server email login ensures end-to-end encryption of emails, protecting them from prying eyes.
b. User Convenience: With SSO, users no longer need to remember multiple login credentials. They can log in to their email accounts using a single set of credentials, saving time and reducing the likelihood of forgotten passwords.
c. Centralized Access Control: SSO provides centralized control over user access. Administrators can easily grant or revoke access to email accounts, ensuring only authorized individuals can access sensitive information.
d. Simplified User Management: SSO simplifies user management for organizations. When an employee joins or leaves the company, their access to email can be easily managed through a centralized SSO system, reducing administrative overhead.
Implementing SSO Secure Server Email Login
a. Choose an SSO Provider: Select a reputable SSO provider that offers robust security features and integrates well with your existing email server. Some popular SSO providers include Okta, Azure AD, and OneLogin.
b. Configure SSO for Email Login: Follow the documentation provided by your chosen SSO provider to configure SSO for email login. This typically involves integrating the SSO provider with your email server and configuring the necessary authentication protocols.
c. Enable Secure Email Protocols: Ensure that your email server supports secure protocols such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS). These protocols encrypt the email traffic between the server and the user, preventing unauthorized interception.
d. Educate Users: Conduct training sessions or provide documentation to educate users about the new SSO secure server email login process. Emphasize the importance of strong passwords, avoiding phishing emails, and other best practices for email security.
Best Practices for SSO Secure Server Email Login
a. Use Strong Passwords: Encourage users to create strong, unique passwords for their email accounts and enable multi-factor authentication whenever possible.
b. Regularly Update Software: Keep your SSO provider, email server software, and email clients up to date with the latest security patches to protect against known vulnerabilities.
c. Monitor and Audit: Implement monitoring and auditing mechanisms to detect any suspicious activities or unauthorized access attempts. Regularly review logs and reports to identify potential security incidents.
d. Provide Security Awareness Training: Continuously educate users about email security, common phishing techniques, and how to identify and report suspicious emails or activities.
Conclusion
SSO Secure Server Email Login is a powerful solution for enhancing email security, simplifying user access, and protecting sensitive information. By implementing SSO and combining it with a secure server, you can significantly reduce the risk of data breaches and unauthorized access to your email communications. Make sure to choose a reliable SSO provider like Pure ID , follow best practices, and educate users about email security to maximize the effectiveness of your SSO secure server email login implementation. Stay proactive in safeguarding your email communications and enjoy the benefits of a secure and convenient email experience.
Power of Unified Endpoint Management Solutions
In today’s digital landscape, organizations are grappling with the management and security challenges posed by the proliferation of devices. From desktops and laptops to smartphones and tablets, the diverse array of endpoints can be overwhelming to control and protect. However, thanks to the advent of Unified Endpoint Management (UEM) solutions, businesses can now efficiently manage and secure their endpoints from a single, centralized platform. In this blog post, we will explore the benefits and features of UEM software and discuss how it can revolutionize device control and security in the modern enterprise.
Understanding Unified Endpoint Management Solutions
To begin our exploration, let’s define Unified Endpoint Management (UEM). UEM is a comprehensive approach to managing and securing all endpoints, including desktops, laptops, smartphones, tablets, and IoT devices, through a unified platform. It enables IT administrators to streamline device management tasks, such as software distribution, configuration, and updates, as well as enforce security policies across all endpoints, irrespective of their operating systems or locations.
Key Benefits of Unified Endpoint Management Software
2.1 Centralized Management:
UEM software provides a centralized console that offers a holistic view of all endpoints, allowing administrators to monitor, manage, and troubleshoot devices from a single interface. This streamlines IT operations, reduces administrative overhead, and improves efficiency.
2.2 Simplified Device Provisioning:
With UEM, IT teams can easily provision new devices by automating the setup process. Configuration settings, software installations, and security policies can be pre-defined and pushed to devices, ensuring consistency and reducing the time required for manual setup.
2.3 Enhanced Security:
UEM software plays a crucial role in safeguarding endpoints from potential threats. It allows administrators to enforce security policies, such as device encryption, password complexity, and application whitelisting, ensuring compliance and protecting sensitive data. Furthermore, UEM enables remote device lock and data wipe capabilities, enhancing data security in case of loss or theft.
2.4 Improved Productivity:
UEM software empowers end-users by providing them with a seamless experience across devices. Employees can access their data and applications from any endpoint, enabling flexible work arrangements and enhancing productivity. UEM also facilitates self-service options, empowering end-users to install approved applications or perform routine tasks without IT assistance.
Section 3: Key Features of Unified Endpoint Management Solutions
3.1 Device Inventory and Tracking:
UEM software offers comprehensive device inventory capabilities, allowing administrators to track and manage all endpoints within the organization. This includes information on hardware specifications, software installations, and device usage patterns, which assists in making informed decisions regarding resource allocation and device retirement.
3.2 Software Distribution and Patch Management:
UEM enables centralized software distribution, ensuring that devices are equipped with the latest applications and updates. It also facilitates patch management by automating the deployment of security patches and updates across all endpoints, reducing vulnerabilities and enhancing the overall security posture.
3.3 Mobile Device Management (MDM):
UEM software includes MDM functionalities that enable organizations to manage and secure mobile devices. It offers features like device enrollment, remote configuration, app management, and data protection, ensuring comprehensive control and security for smartphones and tablets.
3.4 Endpoint Compliance and Policy Enforcement:
UEM allows administrators to define and enforce security policies across all endpoints, ensuring compliance with regulatory requirements and internal standards. It provides real-time monitoring and alerts for policy violations, enabling proactive remediation to maintain a secure environment.
Which unified endpoint management solutions we offer?
SureMDM
With SureMDM we can develop a project solution that drives online revenues.
Surefox
We can develop a project solution that drives online revenues.
Surelock
We can develop a project solution that drives online revenues.
Astro Contacts
We can develop a project solution that drives online revenues.
Conclusion
Unified Endpoint Management (UEM) software is a game-changer for organizations seeking efficient device control and robust security. By centralizing device management, simplifying provisioning, enhancing security measures, and improving productivity, UEM software empowers businesses to navigate the complex endpoint landscape with ease. Embracing UEM can help organizations streamline operations, protect sensitive data, and unlock the full potential of their endpoints in the digital age. Invest in a reliable UEM solution today to elevate your device management and security capabilities to new heights. Contact us at GreenEdge Computers to know more.
Safeguarding Corporate Email Security: Keeping Your Emails Safe
In today’s digital world, email is an important way businesses communicate. But did you know that emails can be vulnerable to hackers and cyber threats? It’s crucial to protect your email from these risks. Let’s explore why email security is important and how Green Edge Computers can help keep your information safe.
Why is Email Security Important?
Emails often contain private information like passwords, financial details, and sensitive customer data. If not protected, hackers can steal this information or infect your computer with harmful viruses. By securing your email, you ensure the confidentiality of your communications and maintain trust with clients and partners.
Common Email Security Threats:
- Phishing Attacks: Some emails may look real but are actually scams trying to trick you into revealing personal information. They may ask for your passwords or financial details. Be cautious and double-check the email’s source before sharing any sensitive data.
- Malware and Ransomware: Attachments or links in emails can contain dangerous software that can harm your computer or even hold your files hostage. Avoid opening attachments or clicking on suspicious links to protect your device and data.
- Email Spoofing: Cybercriminals can pretend to be someone else by faking the sender’s email address. They might impersonate your bank or a trusted company to deceive you into sharing sensitive information. Be skeptical of unexpected emails asking for personal details.
Green Edge Computers’ Solutions for Secure Email:
Green Edge Computers understands the importance of email security and offers solutions to keep your information safe.
- Email Encryption: Green Edge Computers uses advanced encryption techniques to protect your email content. Encryption makes your emails unreadable to unauthorized individuals, ensuring that only the intended recipients can access them.
- Spam and Malware Filtering: To prevent malicious emails from reaching your inbox, Green Edge Computers employs filters that detect and block spam and harmful content. This reduces the risk of falling victim to phishing attempts or downloading harmful files.
- Two-Factor Authentication (2FA): Adding an extra layer of security, Green Edge Computers recommends enabling two-factor authentication. This means you need a second verification step, like a unique code sent to your phone, to access your email. It helps ensure that even if someone knows your password, they can’t access your account without the additional code.
- Employee Training: Green Edge Computers emphasizes the importance of educating employees about email security. They provide training to help recognize phishing attempts, suspicious attachments, and risky online behaviors. By educating your employees, you create a stronger defense against email threats.
Best Practices for Email Security:
Apart from Green Edge Computers’ solutions, here are some best practices to enhance your email security:
- Keep your software and devices updated with the latest security patches.
- Use strong passwords and avoid reusing them for different accounts.
- Think twice before clicking on links or opening attachments from unfamiliar sources.
- Regularly back up your email data to ensure you can recover it in case of any issues.
Conclusion:
Email security is crucial for businesses of all sizes. By implementing the solutions provided by Green Edge Computers and following best practices, you can protect your email from cyber threats. Safeguarding your email ensures the confidentiality of your communications, maintains trust, and keeps your sensitive information secure. Contact Us to know more about our service
Best Unified Endpoint Management Software
Unified Endpoint Management (UEM) is a comprehensive approach to managing and securing all endpoints in an organization’s network, including desktops, laptops, smartphones, tablets, and other connected devices. It provides a centralized platform for IT administrators to manage, monitor, and secure these endpoints, improving operational efficiency and enhancing security posture. In this blog post, we will explore the concept of UEM and discuss some of the best practices and solutions in the field.
What is Unified Endpoint Management (UEM)?
Unified Endpoint Management is an evolution of traditional endpoint management approaches that focus on individual device types, such as Sure Mobile Device Management (MDM) for mobile devices or Client Management Tools (CMT) for desktops and laptops. UEM consolidates these disparate management tools into a single platform, enabling organizations to streamline their management processes and gain better visibility and control over all their endpoints.
Implementing a UEM strategy offers several benefits for organizations, including:
Benefits of Unified Endpoint Management:
- Centralized Management: UEM provides a centralized console or dashboard that allows administrators to manage all endpoints from a single interface. This streamlines management tasks, reduces administrative overhead, and improves operational efficiency.
- Improved Security: UEM solutions enable organizations to enforce security policies, manage software updates, and implement data protection measures across all endpoints. This helps to mitigate security risks and ensures compliance with regulatory requirements.
- Enhanced Productivity: UEM allows for efficient software distribution, remote troubleshooting, and policy enforcement. It improves endpoint performance, reduces downtime, and increases end-user productivity.
- Flexibility and Scalability: UEM supports a wide range of endpoint types and operating systems, making it adaptable to diverse IT environments. It also provides scalability, allowing organizations to easily onboard new devices as their needs evolve.
- Cost Savings: By consolidating management tools and processes, UEM reduces the need for multiple licenses and minimizes administrative overhead. This can result in cost savings for organizations in the long run.
Key Features and Capabilities of UEM:
When evaluating UEM solutions, it’s essential to consider the following key features and capabilities:
- Device Enrollment and Provisioning: UEM solutions should provide easy and efficient ways to enroll and provision devices onto the management platform, supporting both corporate-owned and bring-your-own-device (BYOD) scenarios.
- Configuration and Policy Management: Administrators should be able to define and enforce security policies, device configurations, and software settings across all managed endpoints.
- Application Management: UEM should offer capabilities for managing the entire application lifecycle, including app distribution, updates, and removal, as well as support for both corporate and public app stores.
- Device Security and Compliance: UEM should provide robust security features, such as device encryption, remote lock/wipe, and threat detection. It should also facilitate compliance with regulatory standards and offer reporting and auditing capabilities.
- Patch and Update Management: UEM should allow organizations to efficiently distribute software updates and patches across all managed endpoints, ensuring they are up-to-date and protected against known vulnerabilities.
- Remote Support and Troubleshooting: UEM should enable IT administrators to remotely troubleshoot and support end-users by providing remote control capabilities, real-time monitoring, and remote assistance tools.
- Analytics and Reporting: UEM should offer comprehensive reporting and analytics features, providing insights into device performance, compliance status, and security posture.
Best Unified Endpoint Management Solutions:
There are several UEM solutions available in the market, each with its own set of features and capabilities. Here are a few top UEM solutions to consider:
- VMware Workspace ONE: Workspace ONE is a comprehensive UEM platform that combines device management, application management, and access control capabilities. It offers robust security features, and integration with VMware’s other solutions, and supports various operating systems and device types.
- Microsoft Endpoint Manager: Microsoft Endpoint Manager is a unified management platform that combines Microsoft Intune and Configuration Manager. It provides a single console to manage both traditional and modern devices, with features like policy enforcement, application management, and security controls.
- IBM Security MaaS360: MaaS360 is a cloud-based UEM solution that offers device management, application management, and security features. It provides a user-friendly interface, supports multiple platforms, and includes AI-driven insights for better decision-making.
- Cisco Meraki Systems Manager: Meraki Systems Manager is a cloud-based UEM solution that focuses on simplicity and ease of use. It offers device management, application deployment, and network security features, making it a suitable choice for organizations with distributed environments.
- Jamf Pro: Jamf Pro is a UEM solution specifically designed for managing Apple devices in enterprise environments. It provides comprehensive management capabilities for macOS, iOS, and iPadOS devices, including device enrollment, configuration, and security controls.
These are just a few examples of UEM solutions available in the market. When selecting a UEM solution, it’s important to consider your organization’s specific requirements, budget, and compatibility with existing infrastructure.
Conclusion:
Unified Endpoint Management is becoming increasingly important as organizations embrace diverse endpoint types and face growing security challenges. By adopting a UEM strategy and leveraging the right solution, organizations can achieve centralized management, improved security, and enhanced productivity across their entire endpoint landscape. Evaluate your organization’s needs, explore different UEM solutions, and implement a comprehensive approach to endpoint management to maximize the benefits and secure your digital assets effectively. Contact us at GreenEdge to know more…
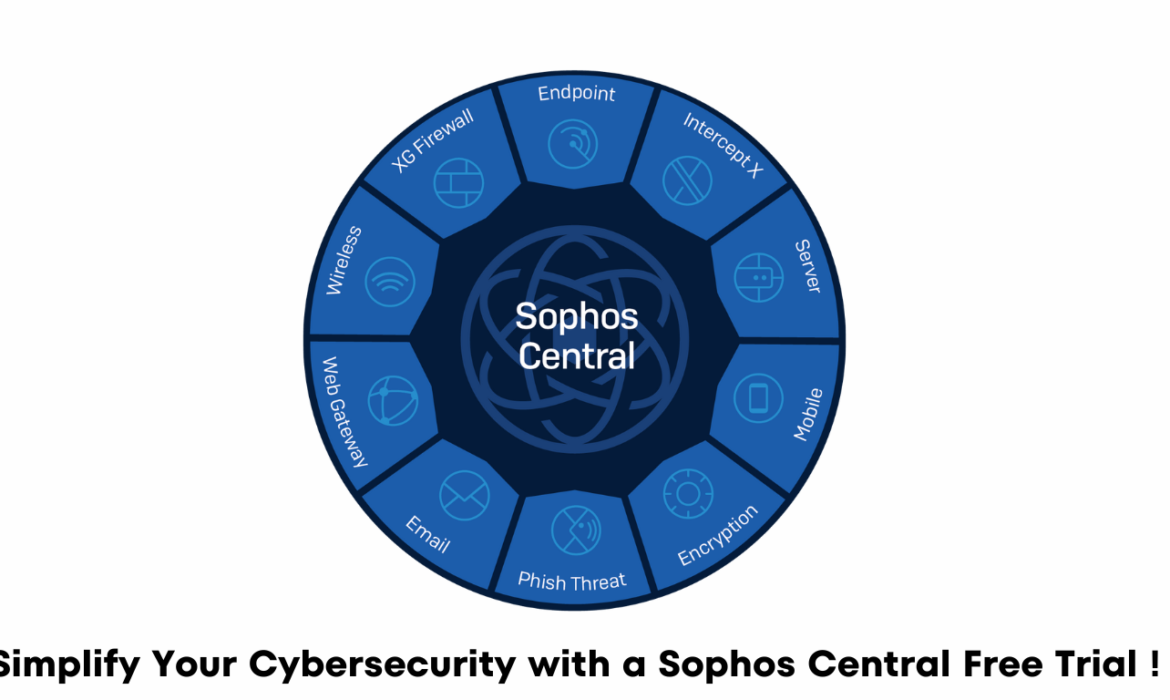
Simplify Your Cybersecurity with a Sophos Central Free Trial !
In today’s digital landscape, protecting your business from cyber threats is of utmost importance. With the ever-evolving nature of cyberattacks, having a robust and comprehensive cybersecurity solution is essential. Sophos Central, a leading cloud-based security platform, offers a suite of powerful tools to safeguard your organization’s digital assets. If you’re considering implementing Sophos Central for your business, you’re in luck! In this blog post, we’ll explore the benefits of Sophos Central and guide you on how to start with a free trial. Let’s dive in!
Why Sophos Central and how to get Sophos central free trial?
- Sophos Central stands out as a comprehensive and user-friendly cybersecurity platform that simplifies threat management for businesses of all sizes. Whether you’re an IT professional or a small business owner, Sophos Central offers an array of features designed to protect your systems and data. Here are a few reasons why Sophos Central is worth considering:
a. Centralized Management:
With Sophos Central, you can manage all your security solutions from a single, unified dashboard. This centralized approach allows for easier policy enforcement, streamlined updates, and better visibility across your organization’s security landscape.
b. Advanced Threat Protection:
Sophos Central combines cutting-edge technologies, such as deep learning and behavioral analysis, to identify and mitigate advanced threats in real-time. By leveraging artificial intelligence and machine learning, Sophos Central offers proactive defense against the latest malware, ransomware, and zero-day attacks.
c. Scalability and Flexibility:
Whether you have a small team or a large enterprise, Sophos Central scales to meet your business needs. As your organization grows, you can easily add or remove licenses and expand your security capabilities without disruption.
Getting Started with sophos central free trial:
- Embarking on a free trial of Sophos Central is a great way to experience its features firsthand and determine if it’s the right fit for your business. Follow these steps to kickstart your free trial:
a. Visit the Sophos Central Website:
Head over to the official Sophos Central website to begin your journey. Look for the “Free Trial” or “Start Free Trial” button, which should be prominently displayed on the homepage.
b. Sign Up for an Account:
Create a new account by providing your basic information, such as your name, email address, and company details. You may also need to select your desired product edition during this process.
c. Choose Your Security Solutions:
Sophos Central offers a range of security products, including endpoint protection, server protection, email security, and more. Select the solutions that align with your organization’s requirements.
d. Set Up Your Environment:
After choosing your desired security solutions, follow the on-screen instructions to configure your Sophos Central environment. You may need to install agents on your endpoints or make necessary network adjustments, depending on the selected solutions.
e. Explore and Evaluate:
Once your environment is set up, take the time to explore the features and functionalities of Sophos Central. Test its performance, assess its user-friendliness, and evaluate its ability to protect your systems and data.
f. Reach Out for Assistance:
During your free trial, if you encounter any issues or have questions, Sophos offers excellent customer support. Take advantage of their resources, including documentation, knowledge base, and contact options, to ensure a smooth trial experience.
Moving Forward with Sophos Central:
- After thoroughly assessing Sophos Central during your free trial, you’ll have a better understanding of its value for your organization. If you decide to continue using Sophos Central, you can seamlessly transition from the trial version to a paid subscription. Sophos offers various licensing options and packages tailored to meet the diverse needs of businesses.
Conclusion:
Sophos Central’s comprehensive security features, centralized management, and advanced threat protection make it an ideal choice for organizations seeking robust cybersecurity solutions. By starting with a free trial, you can experience firsthand the benefits and capabilities of Sophos Central. Don’t compromise your business’s security—take advantage of Sophos Central and protect your digital assets effectively. Get started with sophos central free trial today and experience the power of next-generation cybersecurity!