Phishing Protection solution: SPF, DKIM, DMARC
In this article, we will share with you many phishing protection solution and how you can protect your data against attacks.
There are manifold ways to prevent your business data and email address against spammers and phishers attacks with the help of These three solutions SPF (Sender Policy Framework) DKIM (Domain Keys Identified Email) AND DMARC (Domain-based Message Authentication, Reporting, and Conformance). In this article, we will share with you all the details about SPF, DKIM, and DMARC.
Also read: What is a Firewall and the types of Firewall?
SPF: Sender Policy Framework
SPF (Sender Policy Framework) allows you to confirm that incoming email comes from an original IP address authorized by the sending domain’s administrators.
E-mails from fraud IP addresses marked as “fail” by the sending domain’s administrators are rejected.
Spam & phishing emails often use fraud addresses and with the help of SPF, you can easily protect your data against spam and fraud.
DMARC: Domain-based Message Authentication, Reporting, and Conformance
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email authentication policy & reporting protocol. It builds on both DKIM and SPF protocols to detect & prevent email spoofing attacks. You can also control what happens to messages that fail DMARC checks.
Also read: Phishing Protection solution: SPF, DKIM, DMARC
DKIM: DomainKeys Identified Mail
DKIM (DomainKeys Identified Mail) is an authentication framework used to sign and validate a message based on the domain of the sender. With the help of Sophos’s DKIM solution, You will easily know which email IP address is fraud.
Here are three email protection solutions. You can use these solutions and protect your business’s critical data against malware and phishing attacks.
Reduce Your Attack Surface
Many cyberattacks start with phishing. Sophos helps to unlock end-to-end visibility across your environments, with clear dashboards, detailed threat reports, & extended detection and response.
Also read: Protect your domain reputation and email delivery with SpamTitan
Detect Compromised Mailboxes
Compromised devices lead to your brand & mailboxes being used to spread spam & phishing. Sophos Email security connects with Sophos Endpoint protection to automatically detect & stop these malicious messages.
Build Stronger Security Awareness
Cybersecurity awareness training is an essential aspect of your security strategy. Sophos Email connects with Sophos Phish Threat, an additional service, to identify at-risk users & improve safety awareness through phishing simulations and cybersecurity training modules.
Here is the all phishing protection solution. If you also want to protect your data against spammers and phishing attakers then use these solutions.
Green Edge computers is the trusted partner of Sophos in Dubai. If you also want to protect your business data against malicious attacks and phishing then contact us!
Safetica NXT, next-gen SaaS DLP solution
Safetica NXT – the next-gen SaaS (Software as a Service) best DLP software – now provides truly easy-to-use data safety enhanced with automation & built-in templates. It is continuing Safetica’s tradition of best practices in data protection for SMB (Server Message Block) & small enterprises.
Developed to run and reside natively in the secured cloud, deploying Safetica NXT is possible in minutes. No in-house hardware infrastructure is required.
Once Safetica consumers have been remotely installed on Windows or macOS devices, it takes as little as one day to complete setup & configuration (with the help of Safetica’s new product guide). Then you can immediately audit the full data report, classify sensitive data and start protecting it.
Effective data security needs fast implementation, the least amount of time to administer, & the ability to respond to detected incidents quickly. Safetica’s years of DLP (Data Loss Prevention) experience and focus on easy implementation & use have been acknowledged by Software Reviews. This year, Safetica was recognized as an industry Champion & Gold medalist in the DPL (Data Loss Prevention) marketplace.
Cloud-native DLP Software as a Service
Safetica NXT was designed as a super quick-to-deploy and easy-to-use service that runs natively in the secured cloud.
To run Safetica NXT, you do not need any in-house hardware infrastructure. Simply establish a Safetica Client on your devices & start right away. With the help of a DLP solution, you can easily detect insider threats & risks, prevent data leaks, & record incidents.
Next-gen data security.
Templated data classification
Discover & audit your sensitive data based on built-in templates. Also, audit full data reports in any channel or activity for compliance & forensic evidence.
Incident detection & response
Leverage smart auto-threat detection of incidents & auto-evaluation of risk & doubtful or abnormal behavior for quick response.
Intellectual property and sensitive data protection
With the help of a DLP solution, you are easily able to protect your business and customer-related information from leakage. Also, Prevent mishandling or stealing your data.
Compliance violation detection & mitigation
Detects & audit potential regulatory compliance violations of GDPR, HIPAA, or PCI-DSS & set appropriate security to enforce internal policies.
Simple & smart solution based on the best DLP practices
Safetica NXT has built a risk-driven DLP (Data Loss Prevention) as a next-gen security solution with a particular focus on simplicity & automation. So, administering it needs just a couple of hours per week.
Safetica NXT’s DLP solution provides you with Smart, automated risk evaluation, automated detection of the safe digital workspace, & automatically generated reports making for low-maintenance security.
On-premises solution for data loss prevention (DLP) and insider threat protection, offering enterprise-level features of detection, restriction, UEBA, behavior, & workspace control. Protect your company’s data against insider threats with Safetica’s cloud-native solution. To get more information feel free to contact Greenedge Computers. We are a trusted partner of Safetica NXT in Dubai.
Best IT infrastructure monitoring software
In this article, we will try to cover all information about Motadata’s best IT infrastructure monitoring software. Green Edge Computers are a trusted partner of Motadata in Dubai.
With a single & common platform for network monitoring, log indexing, visualizing, & alerting on all events across your hybrid infra, Motadata helps IT operations leaders provide better business outcomes via Data-Driven intelligence. It discovers & monitors the cloud services, VMs, containers, networks, devices, logs, events, & much more under one advanced AI-powered platform.
Also read: Protect your domain reputation and email delivery with SpamTitan
Nothing Stays Unmonitored
Motadata AIOps delivers extensive data collection capabilities both with the agent & agent-less methods across your on-premise, cloud, & hybrid infra.
- Motadata helps you Access monitoring apps for thousands of devices and technologies across your network, server, application, & cloud layer.
- With the help of an agent or agent-less methods, you collect everything including metrics, logs, events, traffic, and streaming data.
- Eliminate all point monitoring tools by bringing all your network monitoring data to one place to gain deep visibility.
Faster Deployment and Auto Configuration
With the use of auto-discovery and pre-defined monitoring apps, your hybrid infrastructure resources are seamlessly added to Motadata AIOps in real-time.
- Topology Views: See constantly changing IT relationships based on discovery protocols & even network traffic conversations.
- Dashboards & Reports: Comprehensive visualization & dashboard capabilities that take your network monitoring experience to the next level that needs no query language.
- Advance Data Explorers: The advanced & AI-Driven data explorers help you to understand data & track the impact of every metric/process running in your stack.
Also read: What is Datto DRaaS? | Disaster Recovery as a Service Explained
The Right Signals
DevOps & IT infrastructure teams require the right event context to confidently identify the critical and the not-so-critical problems.
- This Machine learning-powered alerting gives capabilities to extract meaningful insight to separate signals from noise.
- Real-time scanning for auto-discovery & dependency mapping to correlate IT service dependencies.
- Low-level data collection on agents – as low as every second for rapid identification & resolution.
A Perfect Solution for an automated network Performance Monitoring
Monitor every bit of your IT infrastructure with a multiple-vendor Network Monitoring Management System.
- On-Premises
- Private Cloud
- Public Cloud
Motadata provides you with the perfect solutions for automated network performance monitoring.
Also read: Mobile Device Management Software
How to set up a network monitoring system?
In today’s world, many Monitoring Management systems are available on the market. They vary in complexity and cost. The most basic network monitoring systems are usually free or have a low price and provide you the very basic functions such as email alerts for device failures or bandwidth usage alerts. More developed and advanced systems like Motadata offer our clients more features such as graphing, reporting, and alerting on specific events like port scans or failed logins.
The best IT infrastructure network monitoring system can be set up by following these steps:
- Firstly, Identify the network components and their respective roles.
- Then identify what kind of data you want to monitor, e.g., bandwidth, latency, packet loss, etc.
- Select any software or hardware solution for your requirements.
- Configure the chosen solution according to your requirements and needs.
Motadata provides you the best it infrastructure monitoring software. If you want to get more information about our IT infrastructure Monitoring services then contact us!
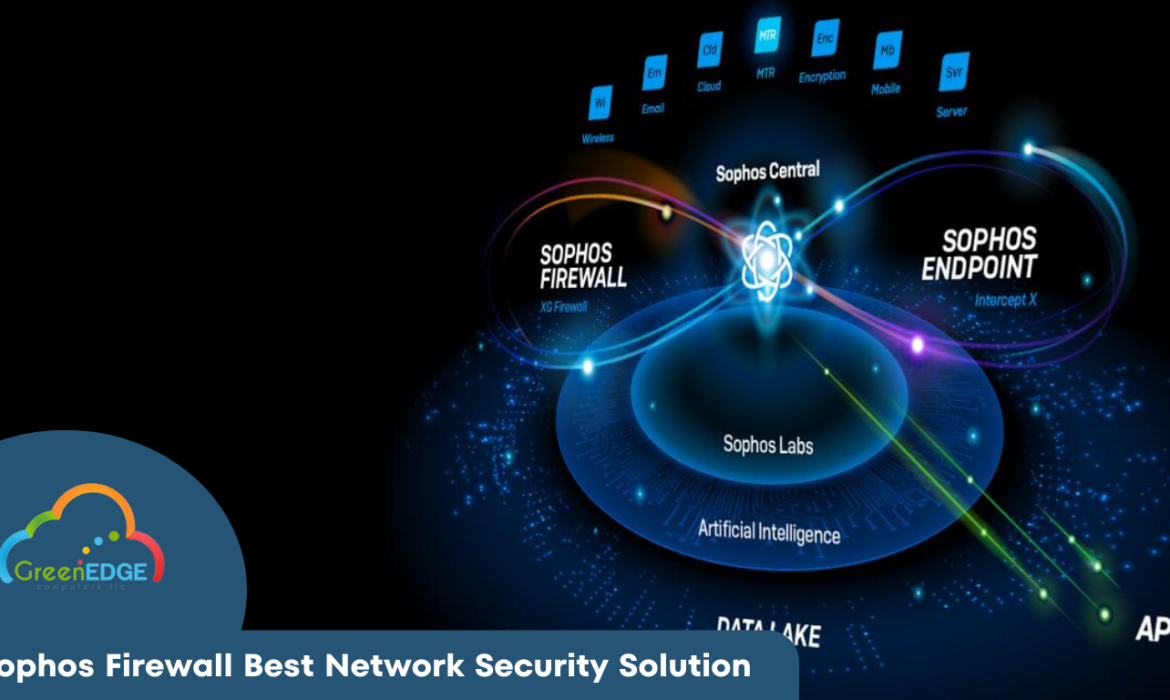
Sophos Firewall Best Network Security Solution
Sophos Firewall offers complete secure boundaries and network security solution with advanced threat protection, deep packet inspection for higher protection, as well as zero-day & ML protection to our clients.
Sophos Firewall is an important layer of protection against malicious traffic attacks and threats targeting corporate and remote users who are traversing today’s hybrid business environment,” Our senior vice president of products at Sophos said. Also, Sophos Firewall’s programmable Xstream Flow Processors enable us to innovate & add new features and capabilities over time, without forcing a hardware upgrade. This provides our customers with a future-proof scalable platform with tremendous value that continues to help to grow with every release.
What services provide Sophos?
Sophos Firewall provides unrivaled network visibility, protection, and response for organizations of all sizes & across all sectors. It also, provides the industry’s best zero-day threat protection, identifying and stopping advanced cyber threats, and its innovative and unique Xstream architecture is engineered to provide our clients extreme levels of performance in accelerating important software-as-a-service (SaaS), software-defined wide area network (SD-WAN) & cloud application traffic.
As a trusted partner of the Sophos Adaptive Cybersecurity Ecosystem, We share real-time threat intelligence with the use of Sophos Firewall Network Protection. Sophos Firewall’s Network solutions and services are faster and more contextual, and synchronized protection, detection, and response. It’s further powered by predictive, real-time & deeply analyzed threat intelligence from Sophos X-Ops, a cross-operational task force linking SophosLabs, Sophos SecOps, & Sophos, & is easily managed in the cloud-native Sophos Central platform or by Sophos MDR (Managed Detection and Response).
Why is Sophos Firewall Network Security solution the best?
Sophos provides the best Network Security solution against cyber attacks, ransomware, and malicious attacks to our clients. Also, Sophos is the best option to secure our business data against threats because this security solution has the best detection capabilities, it has a user-friendly management platform, & Sophos provides you with the best firewall robust solution. That’s why Sophos is the best Network Security Solution.
Greenedge computers is a trusted partner of Sophos in Dubai. We provide the best network security solutions in Dubai. If you want to get more information then contact us at any time!
Protect your domain reputation and email delivery with SpamTitan
SpamTitan provide you the best email data protection. Email Protection Services use multiple layers of security technology that simultaneously work together to offer the best email protection and powerful security. Because attackers and hackers are getting smarter, and threats are continually evolving a powerful email protection service is needed.
SpamTitan offers you wide protection from the most current threats. Moreover, for us, mail filtering is not just another option on a long list of services, it’s our core offering. We provide you with powerful protection that helps you to block inbound threats and secure all outbound data. Also, it helps you to block all dangerous spam, phishing, malware-infected links, and other email threats.
SpamTitan email data protection services help you to protect your data against ransomware, advanced phishing attacks, business email compromise (BEC), spoofing, spam, viruses, and advanced malware threats as they emerge. Every business needs to protect its data from cyber threats. Our thousands of clients depend on our global infrastructure for real-time network intelligence, reputation, and threat detection.
Down below, Greenedge computers share with you all the vital information about SpamTitan’s email protection services.
Also read: What is Datto DRaaS? | Disaster Recovery as a Service Explained
How an Email Protection Service Achieves a High Spam Detection Rate?
An email protection service helps to achieve a high email spam detection rate via a process known as greylisting. When enabled, this process helps you to return your all inbound emails to the originating mail server with a request for the email to be resent. Usually, the email server replies to the request & you get back your email within a few minutes. Spammers and hackers´ mail servers, however, are usually too busy sending out spam to respond to the request & fail to resend the spam email.
With the help of SpamTitan email protection services email has been returned, then the email protection services run it through a series of mechanisms to ensure as much as possible that the email is legitimate. These include checks against Real-Time Blacklists and SURBL databases to find matches with IP addresses from known spammers and hackers, recipient verification checks to ensure each email is addressed to an existent account, & with the use of HELO tests, you’re able to prevent spoofed emails from avoiding detection.
If you want to protect your all informative data then you need to get SpamTitans’ email data protection services. It provides you with the best protection for your businesses against threats, malware, and Ransomware attacks.
How an Email Protection Service Prevents Account Compromises?
One of the benefits of a high spam detection rate is that fewer phishing emails can avoid detection. A powerful and successful phishing attack can result in an employee revealing the login credentials for their email account and an attacker taking over the account with potentially serious consequences. With full control of the email account, an attacker can launch Business Email Compromise (BEC) attacks or use the account to send malware-laden spam emails to the company’s contacts from a “trusted account”.
Also read: Mobile Device Management Software
The benefit of the Spammer of controlling a trusted account
Controlling the trusted account has the benefit of spammers in that many companies whitelist the senders of business-urgent emails to prevent the delivery of their emails from being delayed during the whitelisting process. This means that a spammer could distribute malware through email without any threats being detected at the recipient´s end. This is not even bad for the recipient, but also for the company from which the malware has originated in terms of credibility.
One more risk exists if spam email sent from a corporate email account is detected by the recipient’s email protection service. As well your email getting blocked, and the IP address of the corporate account will be added to a global blacklist. This undoubtedly means that not only is the email address flagged up as a source of spam, but also any other websites associated with the IP address. Email protection service’s outbound scanning feature helps to prevent this scenario from occurring.
Also read: 4 Benefits of Integrating Service Desk with Endpoint Management System
Try SpamTitan´s Email Protection Service for Free
SpamTitan is a very popular and trusted email data protection service that is both easy to use and achieves award-winning spam detection rates (99.97%). Our service can be deployed through the cloud or via an on-premises solution that takes just a few minutes to install in a physical or virtual infrastructure. Thereafter, domain administrators simply log in to the centralized management portal, enable whichever mechanisms they feel are most appropriate to prevent their networks, and adjust the default acceptable spam thresholds if preferred.
One more thing, reports are automatically sent to users when inbound or outbound emails have been quarantined, and real-time & historic text logs are available to administrators with the click of a mouse. Reports can be scheduled to ascertain whether the parameters applied to specific individuals, groups or domains require to be adjusted, & all emails can be retrospectively examined to assist with risk assessments & helps to identify sources of internal threats by spammers.
Greenedge computers are only the trusted partner of SpamTitan. To get more information about SpamTitan, do not hesitate to contact us.
Thanks for reading it!
What is Datto DRaaS? | Disaster Recovery as a Service Explained
Datto provides reliable disaster recovery as a service (DRaaS) solutions and software developed for Managed Service Providers (MSPs) at a flat fee. With Datto’s management services and granular and rapid recovery services & options, you’ll be confident that you can recover in a disaster.
What is DRaaS & Why It’s Important for Your Business?
Datto offers secure data protection products for rapid recovery to our clients. We help you execute and sell the best recovery solutions so you can give next-level business continuity and disaster recovery (BCDR) services. We are always here and ready to provide our amazing services to you.
Also read: Mobile Device Management Software
What is Disaster Recovery as a Service (DRaaS)?
It’s a cloud-based service model. It enables companies to back up data & applications offsite for the fast recovery of companies operations in the event of a local technology failure. Disaster recovery as a service DRaaS is provided by a technology vendor, an IT-managed service provider (MSP), or a combination of the two.
DRaaS provides you with plenty of advantages over traditional on-premises disaster solutions, such as the ability for businesses to access all important data from anywhere, at any time. However, for disaster recovery service DraaS in the cloud-based to be complete, DRaaS is required to be integrated with other elements of the business continuity strategy.
Disaster recovery planning is very helpful in Business continuity. The past few years have seen an increase in the number of disasters that can destroy an IT system, including:
- Natural disasters such as hurricanes, floods, wildfires & earthquakes.
- Equipment failures & power outages.
- The last is Cyberattacks.
Business continuity & DRaaS are crucial processes to ensure your business can keep running in the face of such tragedies.
Also read: 4 Benefits of Integrating Service Desk with Endpoint Management System
A Superior Private Cloud purpose-built for DRaaS
When developing any disaster recovery solution, it’s important to understand how & where your business data is being stored. A public cloud makes you accountable for data protection. At Datto, we try to mitigate that concern with our world-class private cloud. Its immutable features are monitored by a full-time protection team with layered protection capabilities.
Immutable Cloud
An immutable cloud is important for Managed Service Providers (MSPs) looking to provide a reliable data security service for their customers’ data. Essentially, “Immutable” contains many design characteristics, from data that is encrypted at rest to backup files themselves, that can’t be stolen by ransomware. Additionally, access controls such as role-based protection, integration with SSO (Single Sign On), and multi-factor authentication help ensure backup data is safe & available for recovery. The Datto Cloud’s design gives maximum protection & reliability to MSP (Managed Service Provider) clients.
Also read: Network Traffic Monitoring: Why Network Admins Need Network Traffic Analyzer?
Exabyte class scalability
As your MSP (Managed Service Provider) business grows it’s important to start work with a provider that can scale as fast as you can. With the help of exabyte-class Datto scales, any business of any size, so you don’t need to take any stress about running out of cloud storage. Another benefit of this storage scale is: You are able to recover one or all of your client’s systems at the same time due to the size & scalability of the geographically distributed, secure Datto Cloud.
Availability / powerful
We pride ourselves on providing a strong and reliable cloud with 99.9% availability. Datto Cloud is an ideal environment for DRaaS just because of its advanced features, immutable design, and scalability.
Green edge computers is the only trusted partner of Datto’s in Dubai. If you want to get more information then contact us at any time.
Mobile Device Management Software
Greenedge computers provides the best Mobile Device Management software MDM for your business. We are the an authorized 42gears partner in Dubai. MDM (Mobile Device Management) by 42gears is the most powerful MDM solution & MDM app for Android, iOS/iPadOS, Windows, Linux, and macOS platforms. By using MDM solutions and MDM apps you can secure, monitor, & manage company-owned devices for dedicated use as well as employee-owned devices used to access business data (BYOD). Mobile Device Management Software incorporates all aspects of enterprise mobility via unified endpoint management, including Mobile Application Management, Mobile Content Management, and Mobile Device Management. This SureMDM license also includes access to SureLock for kiosk lockdown, SureFox for a secure lockdown browser, & SureVideo for a safe digital signage solution.
Also read: 4 Benefits of Integrating Service Desk with Endpoint Management System
Why is MDM important?
In today’s modern business world, mobile devices are a basic need of everyone’s that why mobile devices completely replaced desktops. Companies are also increasingly shifting their infrastructure to the cloud, allowing employees to access applications, data, & other resources from anywhere & on any device. This MDM provided companies with greater mobility & flexibility.
However, this new style of mobility has brought along greater cybersecurity risks & made device management even harder to understand and difficult. These all-new challenging things make it critical for businesses to adopt mobile device management (MDM) solutions & software.
MDM Solution for Device Lifecycle Management
Every business mostly asks the question“What is Mobile Device Management?” We don’t set any time to use MDM. You can start to use MDM at any time. Every Enterprise device has different problems and different needs at different points in its life cycle. Using 42gears MDM solutions & software will surely help with every one of those points, helping companies get the best return on investment.
Also read: Network Traffic Monitoring: Why Network Admins Need Network Traffic Analyzer?
Enrollment
Mobile Device Management software provides a comprehensive hub for registering any type of device into your network. Where applicable, the MDM software & solutions mostly works with Android Zero-Touch Enrollment (ZTE), Apple Business Manager, & Windows Autopilot to rapidly build your business device network. You can also manually register devices by installing an on-device MDM app & easily connecting the app to the central MDM console. Plus, you can also enroll employee-owned (BYOD) devices via Android Work Profiles & Apple User Enrollment, & develop a secure virtual space to store all your sensitive data.
Provisioning
Mobile Device Management software makes it simple to provision devices with the apps & content they need. You can use Apple Business Manager or Managed Google Play to push apps, or allow employees to access a safe, exclusive Enterprise App Store. For all secure files, offer employees an exclusive File Store. Also, you can lock devices down to several apps, or a single app, to ensure all employees use devices as intended once you dispose of them. SureMDM’s kiosk lockdown feature allows you to efficiently limit device functionality so devices can serve a dedicated purpose. One more other thing, mobile device management (MDM) software also lets you lock down Internet browsing to pre-approved websites for safe browsing.
Also read: All you need to know about Sophos Intercept X Advanced with XDR
Deployment
Deploying devices to employees can be challenging if security certificates and other important credentials don’t reach every device properly. SureMDM gives you a straightforward way to push and check security certificates at any time, making sure that devices work well once deployed. Another potential problem is that devices may not properly sync to Wi-Fi, but if they are locked down, users can’t reconfigure Wi-Fi. SureMDM’s lockdown solution automatically opens network settings when necessary, even when device settings are normally blocked, making sure everyone can access the Internet at any time after deployment.
Retirement
When it comes time to phase out devices, with the help of MDM software to keep track of devices and ensure they are all factory-reset. You can remotely wipe lost devices as well, to guarantee the data on those devices does not fall into the wrong hands. With employee-owned devices, MDM makes it easy to remove the secure enterprise space from the device.
For more information about lifecycle management, check out the Ultimate Guide to Mobile Device Management.
Also read: How to protect your data from cyber attacks?
Benefits of using MDM Solution Software
Now you can answer the question “what is MDM?” You should see why it matters so much. Choosing to implement an MDM solution with SureMDM provides a lot of benefits:
It saves time by setting up apps and content on various devices at once from a central console and pushing updates.
Apart from that, it decreases maintenance costs by replacing many in-person repairs with remote troubleshooting via MDM software.
It also improves stakeholder confidence by bolstering your network’s security and ease of management.
It makes clear boundaries for worker-owned devices to manage sharp data without overstepping personal boundaries.
Prevent device loss with the help of constant inventory tracking, and use location tracking to find and secure misplaced devices.
Increases productivity by blocking access to games and entertainment via the on-device MDM app.
4 Benefits of Integrating Service Desk with Endpoint Management System
Today’s article is very interesting because in this article we will share with you the amazing benefits of an end point security solution & Integrated service desk.
A service desk is the central point of an IT organization to render services, & the quality of Service desk services defines the perception of being an important & valuable part of the IT organization.
The ongoing transition of companies to adopt cloud infrastructure has forced IT associations to update their service desks, which has vendors adopting cloud capability & smart automation powered by Artificial Intelligence (AI).
This ongoing transition confirms that company processes do not run in silos, especially when rendering services overlaying many different departments.
Integrating a service desk with an end point security solution management system is the best step to breaking down siloed operations. The such integration service desk will drive KPIs that measure their user satisfaction, call volume, time to resolve a ticket, etc.
In this article, we analyze four benefits of integrating a service desk with an endpoint management system.
Also read: Network Traffic Monitoring: Why Network Admins Need Network Traffic Analyzer?
Increased Efficiency of Agents
An Integrated service desk automatically connects the data of a user with the devices they are using, which improves the efficiency of the technician analyzing an issue reported by the user.
An incoming ticket will have all the important information about the devices; for eg: an incident ticket about laptop-related booting problems will have the BIOS version mentioned in the ticket. With that useful information, a technician can easily check whether the BIOS is the old or the latest one.
This kind of visibility ends the necessity for all technicians to ask for data from the requester.
Another integration service desk with end point security solution benefit is that it might reduce the number of escalations needed since relevant data is available for level one technicians.
Better Endpoint Maintenance
In an integrated service desk, a software agent runs at the client machine continuously, monitoring all important parameters & generating alerts when something goes wrong or is missing. This integrated service desk allows technicians to track all changes & monitor required errors in their networks.
Resilient to downtimes organizations make by Proactive monitoring.
Since integrated service technicians can handle all problems before they can impact the organization.
Also read: All you need to know about Sophos Intercept X Advanced with XDR
Better Mapping of Symptoms with the Root Cause
Sometimes problems are not problems but are signs of a problem. When you run an integrated service desk in a siloed way, signs may look like problems since there is a lack of knowledgeable information.
At a service desk, technicians can easily identify symptoms & problems with proper root cause analysis. For eg: a ticket about a user not being able to link to their Wi-Fi may look clear, but the real problem may be the user’s laptop MAC address might not be present in the router device. By fetching the MAC Address technician can easily check, under the all related device section, add it to the router, & telling the user to again restart the Wi-Fi adaptor.
Better Remote Support for End Users
In an integrated desk, a remote user facing problems with his/her devices can generate a ticket, & the technician can quickly understand the format of the whole system. The technician has two options. The first option is to remotely access the device & even initiate patch & software updates to resolve the problems.
The capability to remotely handle any problems boosts the all-over protection of an organization’s IT infrastructure. This instills confidence in the minds of all IT leaders to continuously reap the benefits of remote work.
Also read: How to protect your data from cyber attacks?
Achieve Efficient Service Management with Motadata ServiceOps
Motadata ServiceOps is a perfect solution that integrates the power of ITIL-aligned IT service management with an automated end point security solution to deliver the best user experience & better business value.
Our end point security solution is developed for efficiency that drives down cost, & the maintenance of compliance utilizing its built-in SLA management feature.
You can derive all the above-mentioned benefits from our integrated service desk solution that has a self-service portal, codeless workflows, knowledge base, & CI database to store all important information.
We at Green Edge computers are one of the only trusted partners of Motadata. For more information feel free to contact us!