Network Traffic Monitoring: Why Network Admins Need Network Traffic Analyzer?
Network Traffic Analyzer: Network Performance Management helps businesses in Network traffic monitoring. It is used to review, analyze and manage network traffic for any irregularity.
What is a network traffic analyzer?
A traffic analyzer is a process that can impact network performance, availability, and security. Network traffic monitoring uses several tools and methods to study your computer network-based traffic.
In case networks get busier, the overall speed of these networks slows down. Various different trends are getting famous in the IT infrastructure like an increase in the use of cloud servers, video, VOIP, etc. These trends put immense pressure on IT infrastructure resources. When the load on any network increases, companies monitor network traffic with the help of Network monitoring software.
How much does network monitoring costs?
The process of network monitoring is not only expensive but is also useful for a very short period. When you offer more IT infrastructure resources to the network but do not care to lower the pressure, the infrastructure faces identical problems which it was facing prior to the upgrade.
The best way to find out the kind of network traffic and its source is the Netflow analyzers. Simply, Netflow is a feature that was first presented in Cisco devices. This feature can collect IP-based network traffic by monitoring the inflow and outflow of the data. Apart from that this feature helps the administrator to maintain a check on the source and destination of the traffic, class of service, and reasons for congestion. It makes it more manageable to understand the network traffic and manage it properly. I believe you’ve heard the quote from Peter Drucker (Management Guru) “What Gets Measured, Gets Managed”.
Why does the Network Admin Need Network Traffic Monitoring?
There are various reasons to monitor overall traffic on the network. Admins can use the information created by the network traffic monitoring tools in numerous IT operational and security use cases.
- To find out security vulnerabilities and
- To troubleshoot network-related issues
- To analyze the impact of new applications on the overall network
However not all the tools for monitoring network traffic are identical. Usually, they are divided into two broad types
Deep packet inspection tools
Flow-based tools
Further, you have the choice of tools that do not need software agents or tools. Also, they store historical data, and tools with intrusion detection systems. These monitor network traffic within the network as well as along the network edge.
#1. Internal network visibility
Network flow monitoring software that supports protocols such as Netflow, IPFix, JFlow, sFlow, etc. provides full visibility of internal network traffic. With Motadata, the IT department can get insightful reports about the following types and kinds of traffic
- Traffic for Top Applications
- Traffic for Top Conversations
- Traffic Destinations with Host IP
- Top Traffic Sources With IP address
- Top Traffic Receivers with IP
- IP to IP Traffic
- Protocol-Traffic
- Port Traffic
- Application Traffic
#2. Identification of slow applications
Speed or performance has an important role in user experience. One of the most submitted help desk tickets is about the application (web application, Go-to-Meeting, Skype, etc.) being slow or getting crashed. There can be several reasons out of which only one or two will be applicable at any certain time. Identifying these reasons is not only time-consuming but expensive as well. The next-generation Netflow software can filter and report the exact cause. By incorporating the internal data reports with the external resources, the system admins can know a lot about the system and the flawed network.
#3. Detection of spyware and other hacks
When spyware attacks your network, they form a very uncommon data flow in and out. With the help of Netflow, these uncommon patterns can be detected easily. If you are not using some data analyzer, these patterns often go unchecked because these are created to fool the human administrator.
Generally, these worms often generate non-financial problems by making a bad image for the company. However, sometimes, the effect of these worms can have high rates of financial loss as well.
Conclusion
Netflow is a trustworthy and widely supported protocol, Motadata platform supports Netflow (versions: v5, v9), IPFix, sFlow, and JFlow. You must try the Motadata Network Traffic Analyzer tool today and see how it works. Try! It is free for 30 days! Contact us at GreenEdge Computers to know more.
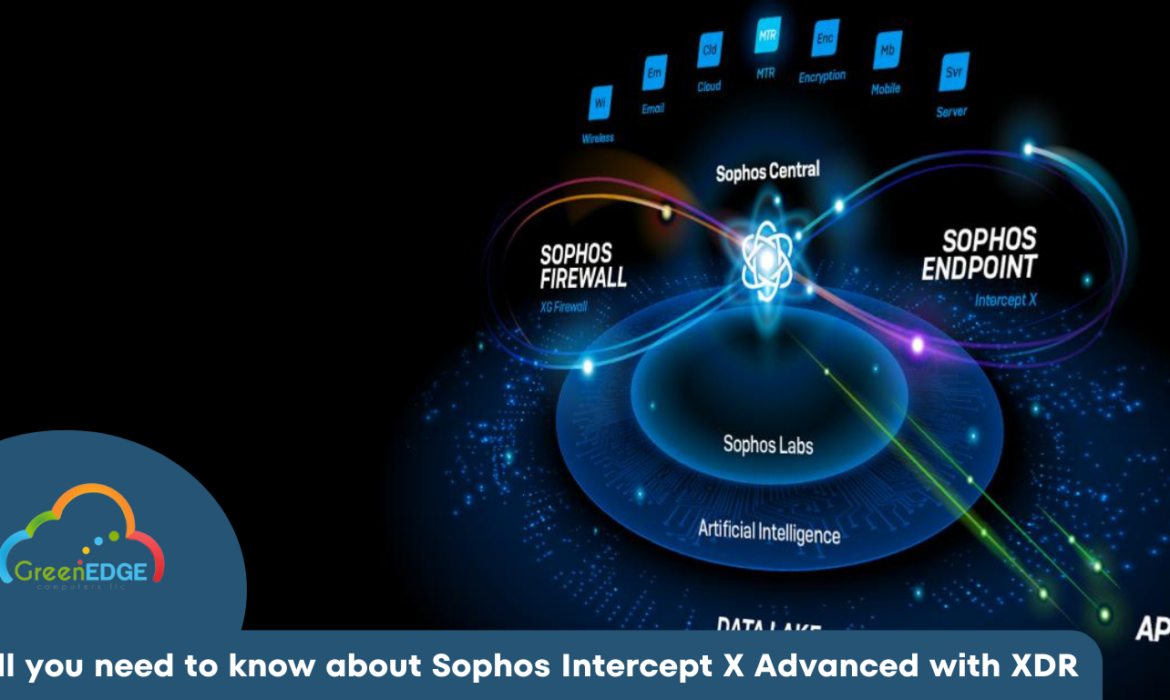
All you need to know about Sophos Intercept X Advanced with XDR
Sophos Intercept X Advanced with XDR incorporates powerful endpoint detection and response (EDR) with the industry’s excellent endpoint protection. It is built for both IT security operations and threat hunting. Apart from that, Intercept X detects and investigates suspicious activity with AI-driven analysis. Sophos also protects all your business endpoints on all your platforms.
Since it works across all your desktops, laptops, servers, tablets, and mobile devices, you can get complete protection for all your endpoints. Let’s explore more about Sophos:
Stop Ransomware in Its Tracks
Sophos blocks ransomware attacks before they bring havoc to your business. Intercept X with XDR contains anti-ransomware technology. This technology detects malicious encryption techniques and locks them down before they can circulate across your network. In simple words, it prevents both file-based and master boot record ransomware.
All encrypted files are rolled back to a safe state. It means your employees can keep working uninterrupted, with the tiniest effect on business continuity. It gives you detailed post-cleanup information, which helps you to see where the threat got in, what it caused, and when it was blocked.
Benefits of Sophos Intercept X:
In this section, we will discuss the major benefits of Sophos Central Intercept X Advanced with EDR. It allows you to ask to see what happened in the past, and what is happening now on your endpoints. Hunt threats to catch active adversaries or leverage for IT operations to support IT security hygiene. When an issue is discovered remotely Sophos central response with accuracy. By starting with the strongest protection, Intercept X stops infringements before they begin. It cuts down the number of objects to investigate and saves you time.
- The strongest protection integrated with powerful EDR
- Add expertise, not headcount
- Built for IT operations and threat hunting
Top Features of Extended Detection and Response (XDR)
We can say that the intercept X advanced with XDR is the only XDR solution that synchronizes native endpoints, servers, firewalls, email, cloud, and security in the industry. It has a holistic perspective of your company’s environment with the richest data set and deep research for threat detection, investigation, and response for dedicated teams and IT admins.
- Cross-reference indicators including from numerous data sources to quickly recognize, pinpoint and balance a threat.
- Furthermore, it uses ATP and IPS events from the firewall to examine suspicious hosts and recognize unprotected devices across your system.
- Sophos Central also understands office network problems and which application is causing them.
- Last but not the least, it identifies unmanaged, guest, and IoT devices across your company’s environment.
Advantages of Extended Detection and Response (XDR)
- Threat Hunting
It is proactive 24/7 hunting by our privileged team of threat analysts. Sophos Central determines the potential impact and context of dangers to your business.
- Response
Sophos Central also initiates actions to remotely disrupt, contain, and neutralize threats on your behalf to stop even the most sophisticated threats.
- Continuous Improvement
With Sophos, you will get actionable advice for managing the root cause of frequent incidents to prevent them from happening again.
We at GreenEdge Computers are the only partners of Sophos Central in UAE. If you want to get more details, feel free to contact us.
How to protect your data from cyber attacks?
Cyber attack protection: Cybersecurity is a serious issue for businesses and consumers. Cyber attacks can lead to data loss, financial damages, and even physical injuries. Your company needs to protect itself from cyber attacks by using anti-virus software and other cyber security measures.
Use Anti-Virus Software
If you’re serious about protecting your computer, you should install anti-virus software. It’s not just for computers anymore—anti-virus software is also designed to protect mobile devices.
Anti-virus software will scan your device and remove any malware that’s been detected on it so that it doesn’t get into the cloud or onto another computer in the future. Anti-virus programs protect against viruses and Trojans (malicious programs), as well as spyware and other types of malware.
Set Up Firewall
Cyber attack protection can be done by setting up a firewall. The first step to protecting your computer from cyber attacks is setting up a firewall. A firewall is a software or hardware device that monitors and controls incoming and outgoing network traffic. Firewalls can help to protect your computer from viruses, malware, and other threats by blocking them before they get onto your machine.
Firewalls can be installed on a network server or an individual computer, depending on what type of firewall you choose.
Keep software updated
Keeping your software updated is important for several reasons. First, it helps you stay protected against new types of attacks. Second, updates can fix bugs and improve the performance of your device or program. Thirdly, they often include new features that make the product better overall. For example: if you have a computer game that includes a “loot” system where players earn rewards for winning battles with other players online (like Hearthstone), then updating this game will mean you’ll be able to use those rewards in another game as well—or even sell them on eBay! So when an update comes out that adds new features as this one does…you should get it!
Be careful with emails and attachments (open only those you know)
- Don’t open attachments unless you know the sender.
- Don’t open attachments from unknown sources.
- Don’t open unexpected attachments, such as an email from a vendor you’ve never used before (or even just never heard of).
- And don’t do it! If someone sends you an attachment with their name on it, think twice about opening it up in your inbox and reading what’s inside—and if anything looks suspicious, don’t click through right away; instead, look at the full message first before responding directly to that person or opening any other links within their message body text like logos or images—because those places may contain malicious code that could infect your computer system if clicked upon without being properly scanned first!
Avoid high-risk websites
For cyber attack protection, avoid high-risk website. If you’re looking for a new online game, you might want to avoid high-risk websites. High-risk websites are often used by cybercriminals to spread malware and ransomware. They can also be used as phishing scams that trick users into handing over their personal information or banking details.
While some of these sites may seem harmless at first glance, they could be putting your computer at risk if you don’t know what’s going on behind the scenes. Don’t worry—we’ve got some tips on how to stay safe from these malicious sites in this article!
Pay attention to an internet connection, lock screens, passwords
- Use a VPN. A virtual private network (VPN) is a secure way to access the internet from anywhere, even if you have an insecure Wi-Fi connection or public hotspot. It encrypts your data and routes it through an intermediary server before sending it to your computer or phone. This helps protect against hackers who can see what sites you’re visiting by monitoring traffic on the open network (like at Starbucks).
- Make sure your passwords are good. Password security should be as strong as possible—but not too strong! You should use something unique for every website, but don’t make them so long that someone could guess them in one try using only common words like “password,” “123456” or “qwerty” (the old standard keyboard layout). Also, avoid using simple phrases like “let me log In here please.” These are often easy targets because they sound innocent enough until someone tries them out with dictionary attacks: try entering “password” into Google’s search bar instead of typing out those two letters separately! If possible, use two-factor authentication whenever possible; this will require users to enter both their password AND another code sent via text message before being able to gain access
Computer security is important
It’s important to protect your computer from viruses and hackers. It’s also important to protect your data, like passwords and bank information. And it’s even more important to protect the integrity of your business—and the internet as a whole!
Conclusion
Cyber attack protection: It’s important to remember that computer security is a constant battle. The best way to protect yourself is by using anti-virus software, keeping your internet connection locked down, and avoiding websites that seem suspicious. If you follow these steps when browsing online or downloading files from the web, it will help keep your device safe from cyber-attacks. Greenedge computers is one of the best cyber security companies in Dubai. We provide you best cybersecurity services and solutions. For more information contact us now.
How Mimecast works and benefits of using Mimecast
In this article, we will discuss how Mimecast works and the benefits of using Mimecast. Mimecast’s email protection system uses sophisticated, multi-layered detection engines & the latest threat intelligence to prevent malware, spear-phishing, & zero-day attacks. Mimecast delivers 100% malware security, & Mimecast’s email spam check technology gives 99% safety against spam.
Mimecast is a subscription-based service, which implies that before utilizing it, your business must have accessed its email management & protection needs before selecting a plan. The Mimecast subscription service is also fully-integrated, which implies you will not require to buy or utilize another third-party solution to manage certain protection tasks. This is why it is officially billed as a suitable email management company.
Mimecast is compatible with the famous operating systems you’re probably to utilize. In terms of deployment, Mimecast can be established on separate devices or multiple-user machines. The installation options available to businesses contain installing and operating a group policy, utilizing a system center configuration administrator, or utilizing a click-to-run license.
Also read: All you need to know about Cyber attacks
How Mimecast Works?
In this section, we are going to discuss how Mimecast works. Mimecast works by using an identify potential threats and a series of filters to scan incoming email traffic. Once Mimecast identifies the threat then it takes the next step to block all the emails and prevent your inbox from reaching. Mimecast also provides you with many features like email archiving and disaster recovery and it helps you to protect your data against malware and ransomware attacks. Mimecast is a complete email security solution that can help companies to protect their data and helps to improve their productivity. So, here we shared with you full information about how Mimecast works. For more information feel free to contact us at Green Edge Computers.
Who Uses Mimecast?
Mimecast is one of the best solutions for all companies to protect their crucial data against malware and cyber threat and it is used by several notable companies, including Adobe, Hertz, NASA, and Nationwide Insurance.
It is also used by very popular industries, such as finance, healthcare, and government. the companies that handle sensitive information Mimecast is one of the best and latest solutions to protect their data against Malware attacks.
After reading this your mind asks one another question why you only choose Mimecast for email protection so here is the answer to your question about why you should choose.
Why Use Mimecast?
You should use Mimecast because it provides you the several benefits and features than other email security software.
The first and foremost reason is, it helps to keep your business email safe from malware attacks and phishing attacks. It scans all incoming emails & attachments for threats & then quarantines any doubtful content or email. This helps your business to protect you and your employees from potentially dangerous email-borne threats.
Besides, Mimecast can also help you to meet various compliance needs, such as those related to email retention.
Finally, Mimecast’s best email archiving feature ensures that all your business emails are safely stored off-site, making them easy to recover if you ever require them for reference or legal purposes.
Now, we hope you get all answers to your questions about how Mimecast works and why you choose Mimecast. Down below, we also share with you some amazing benefits of using Mimecast.
Benefits of Using Mimecast
Mimecast is the best choice for your business. we’ve listed 4 key advantages of utilizing Mimecast cloud email below:
- Reduced Costs
- Reliability
- Advanced Archiving
- Security
Reduced Costs
With in-house email, not only do you spend for the email forum you utilize, you have to purchase a server to store on the premise. This arrives with extra expenses such as electricity required to power the server, a cooling method to decrease server heating, & staff to maintain the server.
With Mimecast, you only spend a fixed monthly per-user payment to operate the Mimecast cloud email forum. You don’t have to purchase any software or hardware. Mimecast shoulders all responsibility for holding the email forum.
Reliability
How Mimecast works: Mimecast boasts a positively sophisticated disaster recovery infrastructure. For example, Mimecast’s Mailbox Continuity has the power to save employee productivity & business processes by giving you uninterrupted entrance to email during cloud email outages.
Also read: Email security mimecast
Advanced Archiving
When you use in-house email, you have to save & back up your emails. You should confirm that you have enough disk space to keep your archived emails. On top of this, it can usually be challenging to quickly find a detailed email you archived a few months ago.
With the use of Mimecast, email archiving is effortless. For example, Mimecast’s Cloud Archive for Email saves your emails by giving you encrypted, secured storage in various geographically distributed data centers with triplicate copies. Storage space is also never a problem, as the Cloud Archive is favorably scalable. What’s more, Mimecast delivers an industry-leading 7-second search SLA to create your archived emails immediately available.
Security
Because you’re a respected client, Mimecast invests heavily in giving you state-of-the-art email protection. For example, Mimecast’s Targeted Threat Security protects your email in real-time against unexplored & sophisticated attacks. Plus, you accept Spam Multi-Layered Malware security, Secure Messaging, & Encryption, Data Leak Prevention, & Secured Large File Sharing.
These are the most important 4 benefits of using Mimecast. We hope you clearly understand what is Mimecast and how it works.
Also read: All you need to know about data breach
Conclusion:
Mimecast delivers all-in-one secure email services that eliminate complexity & decrease the cost of protecting your email system. Greenedge computers is one of the best email security companies in Dubai. We provide the best Mimecast email security services and solutions for your business. Contact us now.
What is cyber security
In this article, we will share all the information about what is cyber security. Cyber security is a process that covers how to protect devices & services from electronic attacks by nefarious players such as cyberpunks, spammers, & cyber criminals. While some parts of cyber security are specially designed to attack first, most of today’s experts concentrate more on choosing the most suitable way to protect all assets, from computers & smartphones to networks & databases, from attacks.
Cyber protection has been utilized as a catch-all phrase in the media to explain the procedure of protection against every form of cybercrime, from identity robbery to international digital weapons. These tags are valid, but they fail to capture the actual nature of cyber protection for those without a computer science grade or experience in the digital enterprise.
The Scale of the Cyber Security Threat
According to Forbes, 2022 will show us a pack of diverse & threatening cyber protection challenges, everything from supply chain disruption to grown smart device threats to a continued cyber protection talent drought.
According to Cybercrime Magazine, cybercrime will cost the world $10.9 trillion yearly by 2025! Also, global cybercrime costs are predicted to increase by almost 17% yearly over the next 4 years.
Concepts such as the pandemic, cryptocurrency, & the rise in remote working are coming jointly to make target-rich circumstances for prisoners to take benefit of.
Also read: All you need to know about Cyber attacks
How Does Cyber Security Work? The Challenges of Cyber Security
What is cyber security: Cyber protection contains technologies, processes, & methods to protect computer systems, data, & networks from attacks. To best solve the question “what is cyber security” & how cyber security works, we must separate it into a series of subdomains:
Application Security
Application security protects the implementation of different defenses in an organization’s software & services against a diverse range of hazards. This sub-domain needs cyber security professionals to write secure code, design safe application architectures, execute robust information input validation, & more, to minimize the chance of unauthorized entrance or conversion of application resources.
Cloud Security
Cloud security connects to building safe cloud architectures & applications for businesses that use cloud service providers like Amazon Web Services, Google, & Azure, etc.
Identity Management and Data Security
what is cyber security: This subdomain protects activities, frameworks, & processes that enable the authorization & authentication of legitimate someone to an organization’s data systems. These steps involve executing powerful data storage means that ensure the information, whether in transition or residing on a server or computer. In addition, this sub-domain creates greater use of authentication protocols, whether 2-factor or multiple-factors.
Also read: Email security mimecast
Mobile Security
Mobile security is a very big deal today as more individuals depend on mobile devices. This subdomain covers organizational & personal data stored on mobiles like tablets, cell phones, & laptops from different hazards like unauthorized access, device loss or robbery, & malware, viruses, etc. In addition, mobile protection employs authentication & instruction to help amplify security.
Types of Cyber Threats
What is cyber security: In down below we share with you the list of cyber threats:
- Cyberterrorism. This cyber threat is a politically-based attack on computers & information technology to generate harm & create general social upheaval.
- Malware. This most common cyber threat contains ransomware, spyware, viruses, & worms. It can establish harmful software, block access to your computer resources, disrupt the whole system, or covertly share information from your data storage.
- Trojans. Like the mythical Trojan Horse of legend, this cyber attack tricks users into believing they’re extending a harmless file. Rather, once the trojan is in place, it attacks the whole system, generally showing a backdoor that permits access to cyber criminals.
- Botnets. This particularly unattractive attack affects large-scale cyberattacks guided by remotely managed malware-infected devices. Think of it as a string of computers beneath the control of one coordinating cybercriminal. What’s more harmful, compromised computers become part of the botnet system.
These are some most common cyber threats.
Also read: All you need to know about data breach
Conclusion:
We hope you got the answer of what is cyber security: Cybersecurity is the shield of internet-connected systems such as hardware, software, & important data cyber threats. We at Greenedge Computers is one of the best cyber security companies in Dubai. We provide you with the best software that helps you to protect your all-important business data. Contact us now.
Benefits of Using Mimecast
Get the best mimecast login to protect your business data. Mimecast protects a business’s email infrastructure from viruses, ransomware, malware, phishing, & the rise of deep-fake attacks. It does this by deploying a layered cyber stability solution that prevents email-borne infections & decreases data loss by archiving emails.
Mimecast email security has many benefits. In down below we share with you the top 6 benefits of using Mimecast.
Also read: All you need to know about Cyber attacks
Benefits of Using Mimecast Cloud Email
Reduced Costs
With in-house email, not only do you expend for the email platform you utilize, you have to purchase a server to store on the premise. This arrives with extra expenses such as electricity required to power the server, a cooling method to decrease server heating, & staff to maintain the server.
With Mimecast, you only spend a specified monthly per-user payment to use the Mimecast cloud email forum. You don’t have to purchase any software or hardware. Mimecast shoulders all accountability for maintaining the email forum.
Reliability
Mimecast login: Mimecast boasts a positively sophisticated disaster recovery infrastructure. For example, Mimecast’s email box Continuity has the power to save employee productivity & business processes by giving you uninterrupted entrance to email during cloud mail outages.
Advanced Archiving
When you utilize in-house emails, you have to save & back up your emails. You also should confirm that you have enough disk area to store your archived emails. On top of this, it can usually be challenging to instantly find a specific email you archived months ago.
With Mimecast, email archiving is effortless. For example, Mimecast’s Cloud Archive for Email saves your emails by giving encrypted, protected storage in different geographically distributed data centers with triplicate compositions. Storehouse space is also never an issue, as the Cloud Archive is positively scalable. What’s more, Mimecast provides an industry-leading 7-second search SLA to create your archived emails immediately available.
Also read: Email security mimecast
Security
Mimecast login: Since you’re a valued client, Mimecast invests heavily in delivering you advanced email protection. For instance, Mimecast’s Targeted Threat Security safeguards your email in real-time against unexplored & sophisticated attacks. Plus, you acquire Spam Multi-Layered Malware security, Save Messaging, & Encryption, Data Leak Prevention, & Save Large File Sharing.
Availability
Since Mimecast is Internet-based, you could access your email in your browser through any device. In addition, Mimecast has mobile phone apps & desktop apps, which permit you to respond to emails faster, whether on the road or in the office.
Worry-free Email Migration
Mimecast login: Migration to Microsoft 365 from Exchange or another email forum comes with intrinsic risks. During migration, all data can be lost or corrupted & is additionally powerless against protection threats. And since email systems go down during migration, you have to discover ways to decrease downtime.
Mimecast could be used as a safe Microsoft 365 migration tool to help keep data integrity during migration. Its Cloud Archive would minimize any information loss or corruption & its broad-spectrum protection will fight online safety threats. In addition, Mimecast’s Mailbox Continuity assistance will give continual access to your emails during migration.
There are six important benefits of using Mimecast cloud security.
Also read: All you need to know about data breach
Conclusion:
Mimecast provides a dedicated cloud-based data solution for dealing with any email & communication protection, & it excels at what it does. This contains using predictive research & automation to deal with threats. You Could learn more about protecting sensitive company communications by contacting us today.
All you need to know about Cyber attacks
Cyber attack UAE: Cyber attacks in the UAE have rushed in recent years, with thousands of people affected by malware and ransomware. To prevent your business from falling victim to these attacks, you must implement strong cyber security measures.
Conduct a security audit
A security audit is an important step in the prevention of cyber attacks. It involves examining your network and identifying any exposures, such as weak passwords or outdated software patches. You should also test the security of your applications, infrastructure, and data by conducting penetration tests or vulnerability scans with ethical hacking tools. Finally, make sure that employees understand how to protect themselves from phishing emails and other social engineering methods used by hackers to gain access to private information on their computers or smartphones.
Also read: Email security mimecast
Install antivirus software and firewalls
Cyber attack UAE: Antivirus software and firewalls are the first lines of defense against cyber attacks. Both should be installed on all devices, including your phone, tablet, and computer. In addition to keeping your device safe from viruses, antivirus software also helps keep you safe from other malicious apps that can break down or damage data on your device.
Antivirus software should be updated regularly so that it stays up-to-date with the latest threats in the wild. Firewalls are another way you can protect yourself from cyber attacks; they monitor traffic entering or leaving your device and block malicious traffic before it reaches any sensitive data stored on your machine
Ensure your software is always up to date!
- Check for updates regularly.
- Make sure all your software is up to date.
Implement strong password protocols!
Implementing strong password protocols is the best way to prevent cyber attacks. You should use a different password for every account, and never use the same password for multiple accounts (even if it’s your email address). Don’t use personal information in passwords either—don’t include birth dates or names, as these can be easily guessed by an attacker. Also, avoid using common words that are found in dictionaries as part of your passwords!
Also read: All you need to know about data breach
Work with a specialist data protection service
Cyber attack UAE: If you’re serious about protecting your business, then it’s time to call in a specialist data protection service.
A specialist data protection service is a skilled professional who can help you with all of your cyber security needs. They will work with you to assess the current state of play and develop an action plan that takes into account specific threats, vulnerabilities, and weaknesses in your system infrastructure. The specialist service will also provide ongoing support throughout the year so that you have access to qualified advice whenever needed.
Cyber attacks in the UAE have surged in recent years!
Cyber attacks have become more frequent and extreme in recent years. Cybersecurity threats are increasing at a rate of 50% per year.
Cybercriminals can wreak havoc on your business, steal confidential information about customers or employees, and interrupt essential operations for days or even weeks. This is why you need to take steps now to protect yourself from these attacks:
- Don’t rely on patchwork solutions that don’t address all kinds of vulnerabilities at once (for example, antivirus software alone won’t work against sophisticated malware). Instead, focus on using multiple layers of protection like routers; this ensures that no single point of failure exists between different parts of your network (which could leave you vulnerable).
- It also helps prevent hackers from gaining access through any one entry point into your system
Also read: Benefits of data protection software
Conclusion:
Cyber attack UAE: Remember that cyber attacks are becoming more frequent and sophisticated. You should always be vigilant against such attacks. To do this, you need to implement security protocols in your business and ensure that you’re always up-to-date with the latest technologies. If you’re not sure where to start, we recommend consulting with an expert who can help guide you through the process of protecting your organization’s data. We at Green edge computers is one of the best cybersecurity companies in Dubai. We provide you with the best cyber security software that helps to prevent your important business data from cyber attacks. Contact us to get more information about cyber security!
Email security mimecast
Email security mimecast: Mimecast is an email security and archiving service that helps you control the flow of your organization’s communications. The service provides a way to manage, review and archive email messages from any inbox or external destination. You can also search all archived emails in one place—allowing you to quickly locate specific types of messages as well as older versions of text documents such as PDFs and Word documents.
What is Mimecast?
Mimecast is a cloud-based email security and archiving service that provides a comprehensive suite of email security and archiving services for both businesses and consumers. Mimecast is available as a standalone solution or as part of the Mimecast platform.
How does Mimecast work?
Mimecast is a cloud-based email protection and archiving service that uses a clientless architecture. The company’s clients can send emails from any device or platform, including mobile devices, the web, and even desktop computers. Mimecast supports all major protocols like SMTP and IMAP.
Mimecast’s hybrid cloud architecture allows you to access your data whenever it’s needed—whether it be in the office or on the go via an app downloaded onto your phone or tablet. This makes for efficient storage of all your sensitive data at one central location where you only need one password/authentication method to access everything from anywhere with no technical expertise required (and no need for any additional licenses).
How do I access my archived emails?
If you have a paid subscription, the email security Mimecast web portal is your best option for accessing your archive.
If you don’t have a paid subscription but still want access to archived emails, there are several options available:
- Use the mobile app (available on iOS and Android). You can also use this app if you’re using an iPhone or iPad with iOS 11 or later installed. The desktop client works only on Windows computers with at least Windows 7 SP1 installed.
Can I send attachments to external recipients?
Yes, you can send attachments to external recipients. They will be sent in a secure format, and the recipient must have a Mimecast account. This means that the recipient must have a Mimecast account and be set up with the same email address as the sender (and should already have an email address).
Email Security and Archiving Services
The Email security mimecast and Archiving Service is a cloud-based solution that allows you to protect your organization from email-borne threats.
With Mimecast, you can:
- Monitor outgoing messages for suspicious activity or abuse. You’ll receive alerts if one of your employees sends an email that contains malware or phishing links, making it easier for you to block the message before it gets out into the public domain.
- Archive unwanted emails in bulk for easy retrieval later on. With our archiving service, customers can easily search through past messages on their timeframes so they’re never left wondering what happened with any given message—and have peace of mind knowing they won’t be exposed by malicious actors again!
Conclusion
As you can see, Mimecast is a powerful tool that can help you protect your email almost anywhere in the world. If you’re looking for an alternative to Gmail’s archiving features, then Mimecast may be the right choice for you. Greenedge computers is one of the best email security companies in Dubai. Contact us now to get more information about email security Mimecast.
All you need to know about data breach
Data breach: Data breaches are a huge problem for all of us. They can put your personal information at risk, but there are steps you can take to protect yourself from identity theft and fraud. Here’s what to do after a data breach has occurred:
Know that a data breach has occurred!
A data breach is when a user’s information (such as names, addresses, and other personal details) is stolen by hackers or other criminals. The consequences of a data breach can range from inconvenience to identity theft, financial harm, and physical threats.
You should know that if you have been affected by a data breach:
- You may have received an email notifying you of the incident.
- You may have heard about it on the news.
- Your bank may be contacting you with questions about transactions made in your name, or your employer might be sending out an email asking for any information regarding employment fraud at their workplace.
Check your account activity
Check your account activity:
- Check your credit report. If you’re worried about a data breach, it’s important to check your credit report.
- Check other financial accounts that relate to those affected by this breach (e.g., bank accounts). Any unusual activity could indicate fraudulent activity so it’s worth checking these accounts out as well
Change your password and security question/answer!
- Use a strong password. It’s important to use a different password for each account, as well as one that is long and complex. If you don’t know anyone else who might have access to your data, consider using something like “12345678” or “password.” Don’t share your passwords with anyone or write them down anywhere—and don’t use the same one twice!
- Change it regularly. Changing your security questions and answers regularly is another step toward keeping yourself safe from hackers trying to break into your accounts. Remember: It’s always better to be safe than sorry when it comes to cybersecurity issues like these!
If you loss your data and now you are searching how we protect data. So, We suggest you to choose best data recovery software Datto.
Check your credit report and financial accounts!
- Check your credit report.
- Check your financial accounts.
If you find fraudulent activity on any of these accounts, contact the relevant authorities at once. If you notice suspicious behavior in your account(s), like unauthorized charges or changes to passwords, contact the bank or credit card company that issued it immediately and ask them to investigate.
Subscribe to free credit monitoring services!
If you’re worried that your data has been exposed, or if you’re concerned about identity theft, sign up for a free credit monitoring service. These services are not the same as your actual credit report; instead, they allow you to monitor the activity of a third party (such as an employer) who may have accessed your personal information without permission. You can also use these services to detect signs of fraud or other types of unauthorized access.
If a company tries to charge fees after it loses control over its customers’ data—for example, if hackers make off with all the customer records from one retailer’s website—you will be notified by email when this happens so that you can take further action based on what happened and how serious it is.
Continue to check your credit report, financial accounts, emails, and other sensitive information!
You should continue to check your credit report and financial accounts for any suspicious activity.
It’s also a good idea to check your email accounts and other sensitive information like social media profiles for any suspicious activity.
Keep an eye on your accounts after a data breach
After a data breach, it’s important to keep an eye on your accounts.
- Check your credit report and financial accounts. If you’ve been affected by a data breach, check with each of the companies that have had access to your information (like banks or retailers) about whether there has been any unauthorized activity on their part since then. You can also look for suspicious activity in other places where you might not expect it—like Amazon or Netflix—by checking those services’ websites for signs of suspicious behavior or unusual activity.
- Subscribe to free credit monitoring services. These will alert you if someone tries to open new lines of credit under your name, as well as alert you when they try signing up for automatic payments from other sources like utility bills. Also, remember that some companies may offer free plans including this service; check before signing anything!
How to protect your data?
You can protect your data with the help of data recovery software. We give you the best data recovery software Datto. Datto is one of the best recovery software. With the use of Datto, you can easily protect your all-important business data. Datto contains many backup and recovery options.
If anybody steals your data or you can mistakenly delete your data. Then you don’t need to worry if you have Datto recovery software. Because Datto contains many recoveries and backup solutions. You can use these solutions and recover your data.
Conclusion
So what will you do with all this information? You can use it for your protection and keep an eye on your accounts after a data breach. Green edge computers are one of the best data recovery company in Dubai. We provide you with the best data recovery software for your business. For the best data recovery software contact us now:
Benefits of data protection software
The world of data protection is constantly changing. It’s important to stay up-to-date on the latest trends, technology, and threats so that you can make the best decisions for your organization. One of the biggest trends in data protection is cyber attacks. Cybercriminals are constantly coming up with new ways to steal personal information from people around the world—and they’re getting more sophisticated as well!
It keeps you safe from cyber attacks.
It’s not just about protecting your data. It’s also about keeping your computer safe from cyber attacks. Cyber attacks can happen in a variety of ways, but the most common types are phishing and social engineering. Phishing is when someone sends you an email or website link that looks like it’s from another business or organization but leads you to a website where they have stolen your personal information and are trying to sell it somewhere else. Social engineering involves tricking someone into giving up information by impersonating someone they trust (like their boss), tricking them into performing an action on behalf of themselves (such as clicking through a link) or getting them to reveal their PIN so they can access their bank account online—all these things are done through phone calls, emails, texts messages, etc.
It keeps you informed of potential risks.
Data protection software can also help you stay informed of potential risks. For example, if your company is subject to a data breach or other privacy breach, the program will alert you so that you can take steps to prevent further incidents. It’ll also tell you how to fix any issues that might have been caused by the incident (or incidents).
Businesses need to know what information they’re collecting and sharing with other parties for them to comply with all applicable laws and regulations—and this includes keeping tabs on anything that could lead up toward becoming illegal activity.
It can protect your information when a device is lost or stolen.
If you lose your device, it can be a serious problem. If someone finds it and takes it without permission, they could do all kinds of things with the information on their phone or tablet. They could access sensitive data like credit card numbers, email addresses, and passwords.
Data protection software can help protect against this kind of loss by tracking the location of the lost device so that authorities can find it quickly if necessary. It will also lock down the device to prevent anyone else from using its functions until you’ve gotten back what’s yours—and wiped any sensitive data in case they tried to do so themselves while they had control over this machine!
It allows you to track suspicious activity.
Data security software can also help you track suspicious activity. This is especially useful if your device has been infected with a virus, as it will alert you to that fact. It can also detect when someone is spying on you or hacking into your device, which may be dangerous if they have access to the data stored on your device. If someone tries to use malware (malicious software) against you or another person to steal information from their computer systems or steal money by making fraudulent purchases online using stolen credit cards or passwords then this feature will notify them immediately so they know what’s going on!
Finally, some companies prefer using data protection software because of its ability not only to prevent fraud but also to protect intellectual property rights by detecting illegal copying at the source level before further processing occurs (i.e., during transmission).
It always has the latest protection.
As a business owner, you will know how important it is to have the latest protection available on your computer.
When looking for data protection software, you should make sure that the provider has their software updated regularly. This means that they are constantly updating the virus definitions and spyware definitions to ensure that they always have the most advanced protection available. The same goes for firewall definitions: if a company doesn’t update its firewall software often enough, then there will be gaps in functionality between updates which could allow hackers access into your network when they’re trying to break into it!
You should make sure your computer is protected from cyber attacks
You should make sure your computer is protected from cyber-attacks. Cyber attacks are a real threat. It’s important to be prepared and have the latest protection, but you don’t have to spend hundreds of dollars on software just to protect yourself.
There are many free tools available that can help you keep your data safe, like antivirus software or firewalls (also known as network security products). These tools will monitor traffic coming into and going out of your computer so it’s always updated with any changes made by hackers or other bad guys who want access to confidential information stored on your device.
Best data protection software?
Are you looking for the best data protection software for your business? So, now you’re in right place. We at Greenedge computers give you the best especially designed data protection software Datto. Datto is one of the best data recovery software. This software has contain many recovery and backup solutions. So, use this software and protect your all vital business data.
Conclusion:
With all these benefits, it’s no wonder that data protection software is a must-have for any business. Datto helps you protect your data from cyber-attacks and keep your company informed about potential risks. It also allows you to track suspicious activity on all of your devices so that when something does go wrong, there’s no need to panic – because as long as there are backups available in case anything happens, nothing will happen at all!